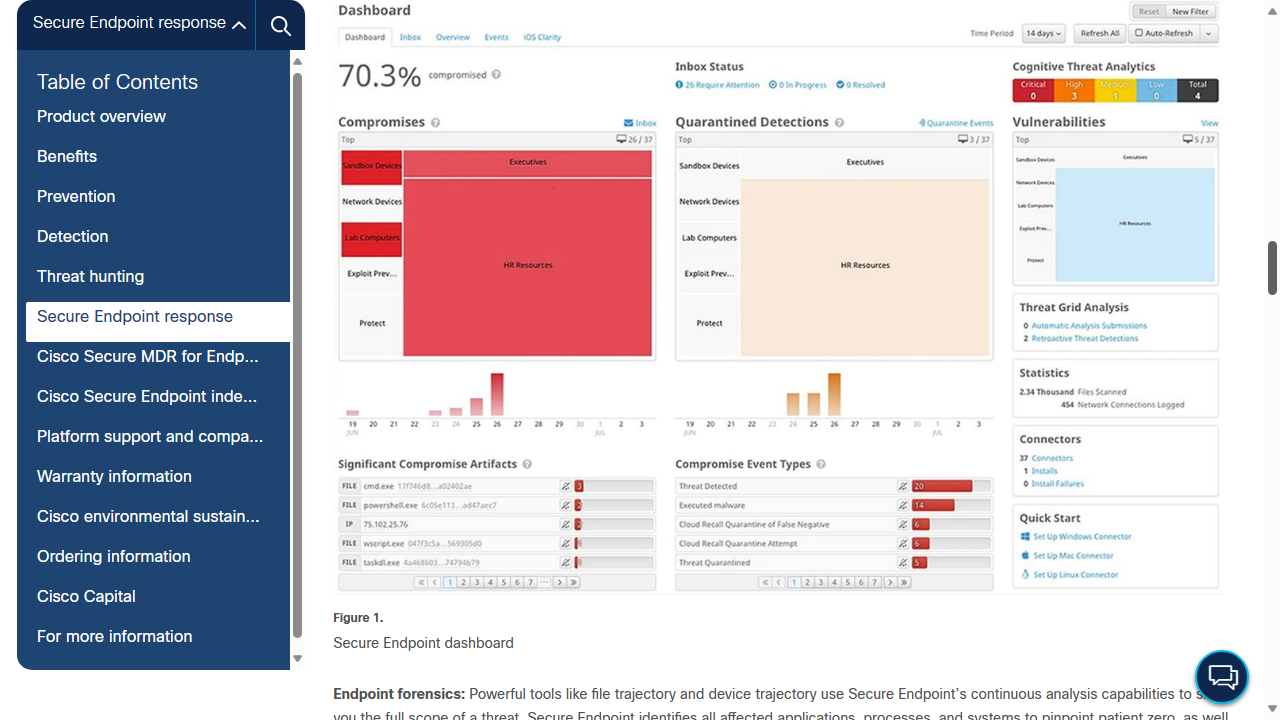
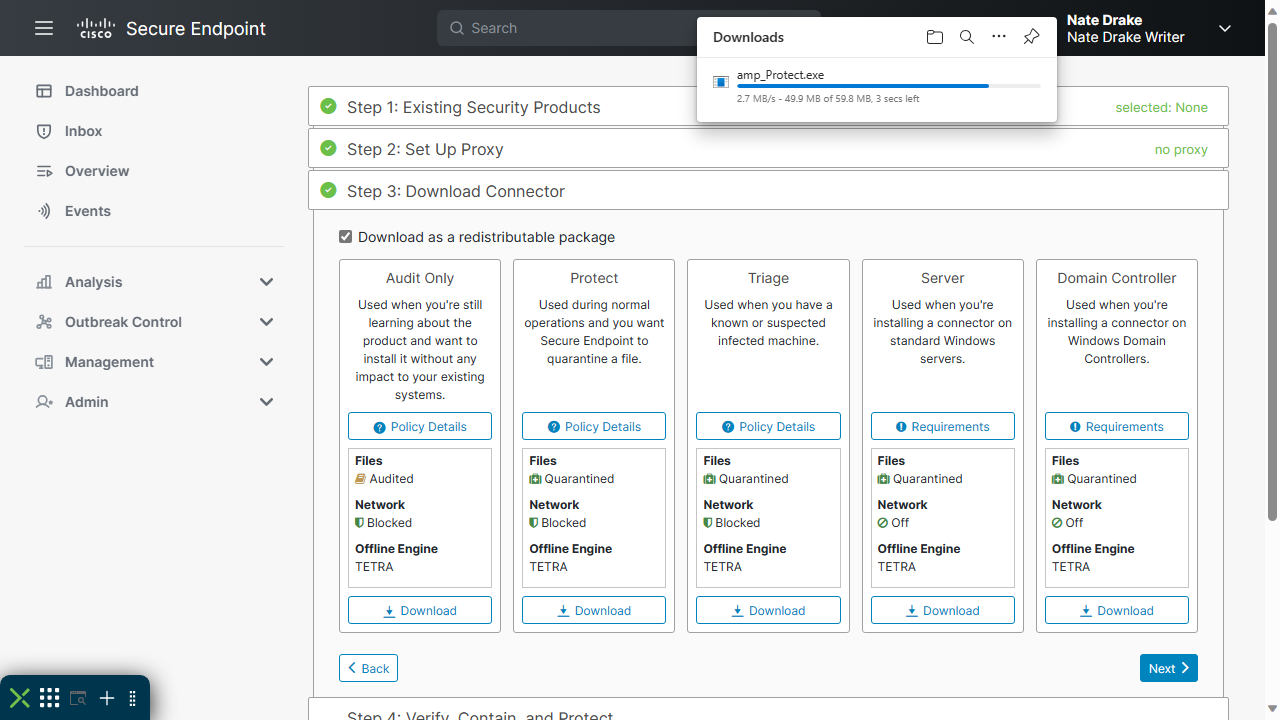
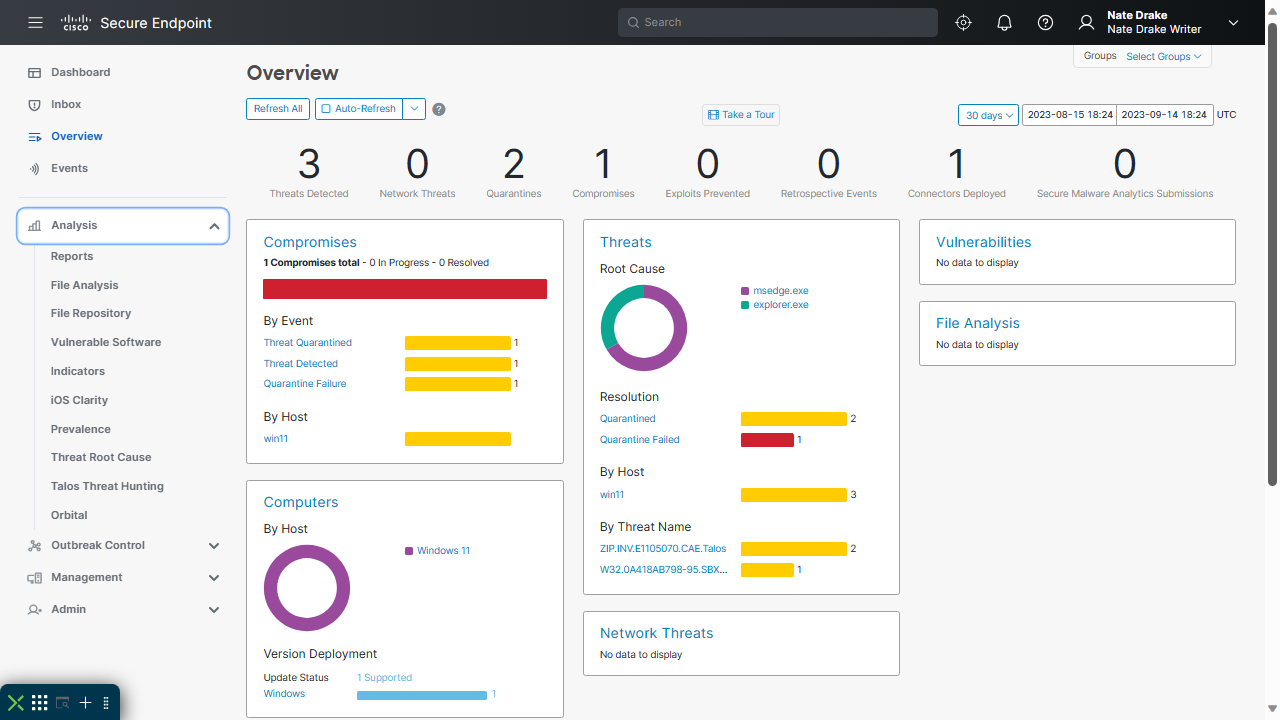
Syxsense was founded in 2012. In its own words, the company focuses on, "a cloud-native unified security and endpoint management (USEM) platform that reduces risk and complexity." In other words, their flagship product is an extremely versatile endpoint security platform.
At TechRadar, we always give credit where its due to security 'Goliaths' like Symanetc and Malwarebytes but also keep an eye out for the less well known 'Davids' who create products that put even the giants to shame.
The question remains though: is Syxsense's platform a Goliath to rank among the best endpoint protection software, or just garden variety?

Syxsense: Plans and pricing
When we visited Syxsense's pricing page, we were unsurprised to see that interested parties are encouraged to contact the company to request a quote. This is par for the course for many endpoint security platforms.
However, when we did set up a free trial of the platform, we discovered the 'Subscriptions' section of the cloud console actually does list costs per device. We are using these for the basis of this review but encourage readers to speak to Syxsense directly for an exact quote.
The most basic tier is called 'Syxsense Manage' and according to the cloud console costs $5 per device, per month. Benefits of the 'Manage' tier include basic device management, patch scans, remote control, the ability to isolate and reboot endpoints, as well as customizable dashboards and reporting features.
These features are what we'd expect to see in an EPP (Endpoint Protection Platform) but you'll need to subscribe to he next tier, 'Syxsense Secure', to actually detect and prevent threats effectively. This costs $8 per device, per month and includes all of the above plus a drag a drop workflow builder, the ability to set policies, vulnerability scans, file quarantine and threat alerts, as well as proof of HIPAA/PCI/SOX compliance.
The highest priced tier, 'Syxsense Enterprise' is the one on which this review is based. According to the cloud console it costs $9 per device, per month. For their extra dollar subscribers benefit from all of the above perks in the first two tiers, plus zero trust, security remediation, mobile device management and an open API.
Interested parties can try out all Syxense features for free for 14 days on up to 50 devices and 50 mobile devices.
Syxsense: Features
Given that we had chosen to review 'Syxsense Enterprise', we were eager to find out more about the benefits it supposedly offers over other endpoint security platforms.
We'd noticed on the pricing page that Syxsense claim the platform employs 'Zero Trust'. This term gets bandied around a lot, even by security professionals so we wanted to be sure that the company meant. Luckily Syxsense maintain a dedicated page, explaining that the platform allows granular control over network access policies. This makes identification of users, as well as ringfencing apps much simpler, which aligns with the principles of 'zero trust'.
Syxsense also have a dedicated page, explaining their 'remediation' feature in more detail. In brief, this involves Syxsense Enterprise using real-time monitoring to identify which assets are vulnerable, how to fix them, and deploy those resolutions quickly and automatically from within the console, without users needing to do anything.
Something that did tickle us when researching Syxsense Enterprise was the 'Beers with Engineers' initiative - this essentially is a 'free lunch' in that the company offers a $25 gift card to representatives of certain companies who are interested in joining a virtual event to learn more about the console.
As far as we know this offering of free food and refreshments to interested parties whilst they learn more about a platform is a first for the field of endpoint security but are sure that it goes over well with larger organizations. We were only sad to see that the offer of free food doesn't extend to reviewers!
Syxsense: Setup
If you opt for the 14-day free trial of Syxsense Enterprise, there's a registration form on the main website. The portal requires a valid business e-mail (in other words, one linked to a registered domain, not a 'free' e-mail provider.)
After entering your contact information, the website next asks you to create a subdomain e.g. ours was natedrake.syxsense.io, which you'll use to access the cloud console. On first login we were impressed to see that 2FA (two-factor authentication) is enabled by default, as we had to enter a code sent to our email address. This can also be done via Google Authenticator.
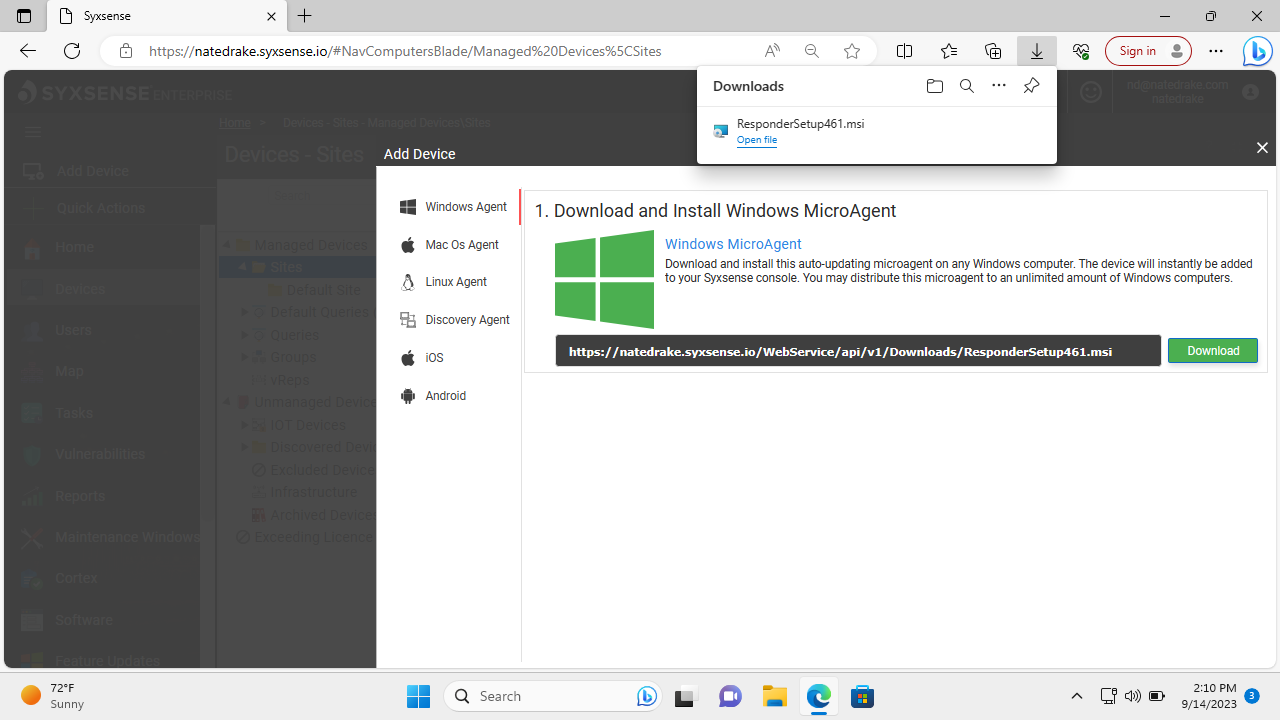
On first login to the cloud console the 'add device' option at the top left was easy to see. We were delighted to discover that agent software is cross-platform, with clients available for Windows, macOS, Linux, Android and iOS.
We downloaded the Windows installer (in MSI format) and launched it. The progress bar appeared but then the installer seemed to exit. On checking the installed programs in Windows 11 we saw the 'Syxsense Responder' did indeed seem to be installed but there was no icon in the system tray.
Upon logging in to the online cloud console we also saw our test endpoint 'Win11' listed but when we tried to run a remote scan to check for vulnerabilities, nothing happened. This was troubling, so we removed the 'Responder' software in Windows and reinstalled, with the same effect.
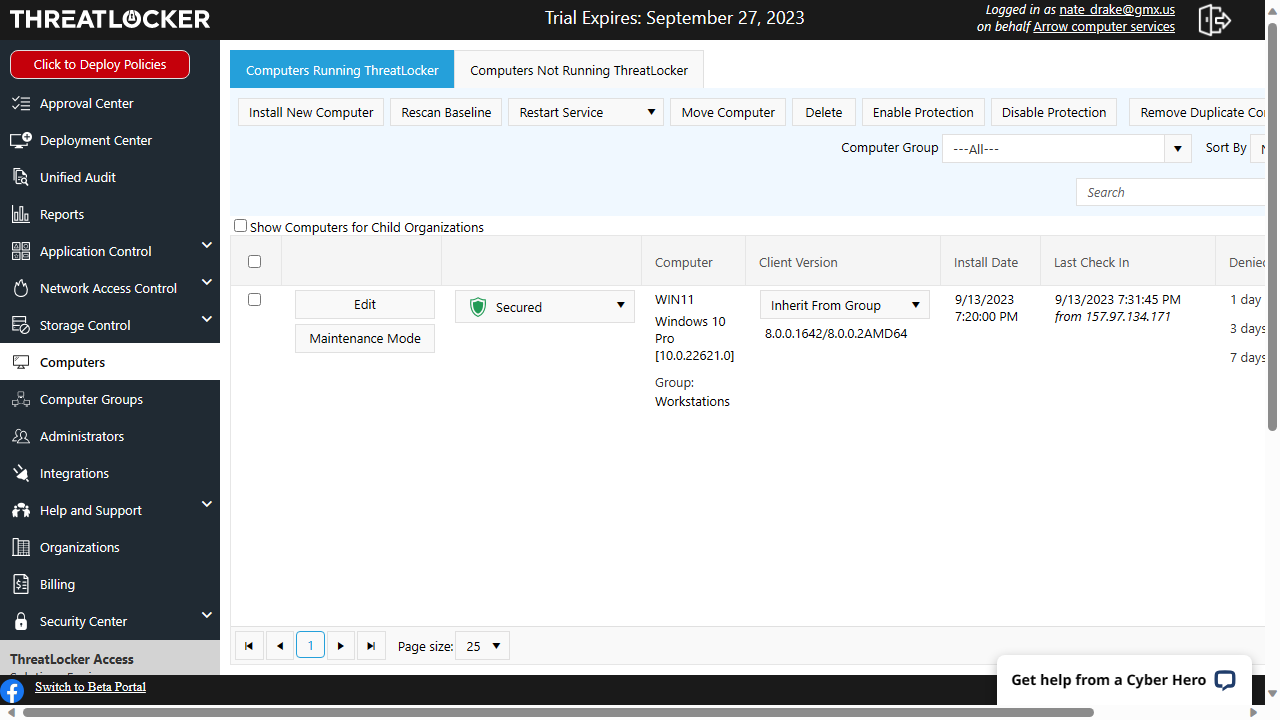
Syxsense: Interface
We've mentioned previously that the 'Add Device' option was easy to find in the online console. Indeed the left hand pane lists options like 'Devices', 'Users', and 'Reports' logically, accompanied by colorful icons.
As readers know, at TechRadar we place great stock in the main 'dashboard' of products and were impressed by the colorful graphics employed in Syxsense Enterprise. The resolution on our test machine's monitor (1280 x 720) resulted in quite an overcrowded screen but immediately became much neater when we switched to 1920x1080.
We were particularly impressed by the 'Overview' section of 'Devices', which displays vital information in dedicated areas. For instance, 'Computer Health' contains information on detected and potential software vulnerabilities. The 'Current Activity' section towards the bottom of the screen lists tasks and their status.
While agent software is usually quite threadbare, we've never had to deal with an invisible one before. With other endpoint security platforms we've reviewed, there's usually a system tray icon which users can click to run scans and/or view any files in quarantine. We aren't sure if the absence of an agent window was by accident or design, but either way it's far better to have a way of informing endpoint users of tasks in progress.
Syxsense: Performance
We've said previously that upon logging into the cloud console and seeing our test device was connected, we tried to run a vulnerability scan. In fact, we tried to do this four times. In each case the device's 'Current Activity' section said the scan had failed, though no specific reason was given.
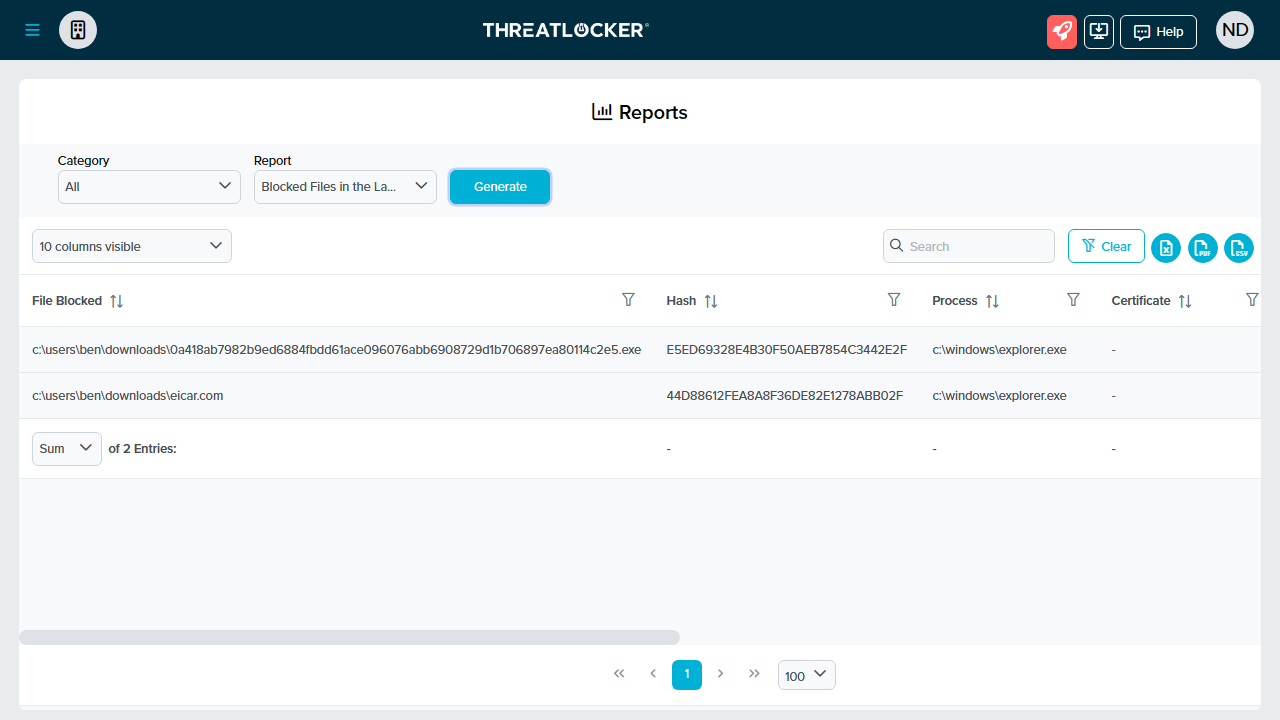
This didn't bode well for our tests but we decided to continue anyway. When reviewing endpoint security platforms, our first test is always to try to download a fake computer virus, provided by the good people of EICAR.
We visited the website in the Microsoft Edge browser on our Windows 11 test machine, then downloaded the fake virus in compressed (ZIP) format. We were able to extract the file but the 'Responder' failed to respond and it fell to Microsoft Defender to block the virus. When we logged in to Syxsense cloud console we also saw no alert had been generated in the 'Reports' section.
Our next test was to attempt to copy a real, new trojan virus to our test machines 'Downloads' folder. We do this when reviewing EPPs to check that they can detect threats based on a file's behavior, not just by comparing its signature to a database of known malware. We were able to copy the file into the folder and once again it was Microsoft Defender which ultimately quarantined it. Once again, the cloud console also failed to generate any alert to say the trojan had been detected.
Syxsense: Final verdict
Having criticized the Syxsense Enterprise platform for a lack of threat detection, we must praise the level of support from company staff. Shortly after signing up for a trial we received a voice message and email from one of the team to ask some questions.
We feel sure that had we persevered and gone through the agent deployment steps again with a member of the team (or better yet attended 'Beers with Engineers'), we may have seen better results with installing both the client software and with detecting the malware files we used in our tests. We simply didn't have the time to do this but the target market for Syxsense Enterprise are organizations with IT Managers who are paid by the hour to resolve such issues.
Still, the fact that agent deployment and basic threat detection doesn't work out of the box is a concern for us, no matter how 'unified' the platform's threat response is supposed to be when working correctly.
On the plus side, setting up the platform is very easy. The cloud console itself is well laid out and the process (if not the execution) of installing agent software on endpoint devices is a breeze. It's also good to find a platform that supports Linux endpoints, as well as mobile devices.
We encourage readers to take advantage of the free trial to see if they can succeed where we failed in test-piloting this endpoint security platform.