One-minute review
A groundbreaking collaboration between Google, Samsung, Apple, Amazon, and a whole mess of other tech companies, the Matter standard is meant to unravel the complexity of smart homes, one Thread-connected device at a time. And the SmartThings Station is Samsung’s first big entry in the Matter world.
The Station is a kinda-clunky smartphone charger with a Matter hub inside it, to connect all your gadgets and unlock the smart-home coolness you’ve been promised: The Station will turn off the lights when you go to bed! It’ll find your missing keys! It’ll make everything work, seamlessly and simply! All for just $60 bucks! Well, $80 if you want the charging brick … and you do.
That said, the Matter standard (and the SmartThings Station by extension) are a promise based on you upgrading all your stuff, or better yet, simply starting from scratch with new gear. And the device itself does little to alleviate the clutter confusion most consumers probably have when it comes to hubs. Do I need one? Wait, I have one already? And I need another? Which spec or protocol am I using anyway?
The Station is simple enough - and smart enough, for that matter. But like a teenager’s bedroom, I’m afraid the smart home may remain a cluttered mess for now.
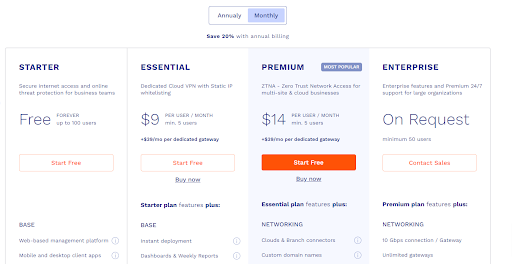
SmartThings Station review: price and availability
- List price: $79.99
- Available only in the US
The is available to buy for a list price of $79.99 and is available only in the United States. It can be bought direct from the Samsung website. You'll have a choice of color to choose from; it's available in black or white.
SmartThings Station review: Specs
SmartThings Station review: Design
The Station is a black plastic square with rounded edges, about an inch tall -- sort of like a stack of drink coasters. A dark gray top is recessed a tiny bit and contains a single button in the top right corner that can activate different features depending on whether you press, long press, or double press it. There’s a set of colored LEDs on the right front edge to indicate connectivity and charging status and a USB-C connection on the back. And that’s about it.
Because it has extra smarts in it that any other charger lacks, it also has a fan to keep itself cool. I didn’t notice the gentle whir at all, but somehow my wife said she heard it on my nightstand from her side of the bed. Pay her no mind; it’s not really audible.
The $60 version of the Station lets you BYO your charger, and you've probably got something around that'll power it via USB-C. But to get super-wicked-fast charging from your Galaxy phone (you're using this with one, right?), you'll want to drop an extra $20 to get Sammy's.
For a phone charger, the Station is decidedly clunky, especially when compared with the $10 Tozo W1 wireless charger I bought recently, a wisp of a disc with a grippy rubber top. (Don’t like the Tozo? We’ve got a great list of the top chargers on the market, which come in all sorts of shapes and sizes.) But keep in mind, this is no mere charger, hence the circa $80 price tag. The Station has a secret: Matter. We’ll get to that in a second.
Design score: 2 out of 5

Let's talk about hubs
The core raison d’etre of the Station is also the main problem with smarthomes today: hubs. (And you’re forgiven if the word alone makes you want to put a pillow over your head.) Some smart home devices connect directly to an app on your phone through Wi-Fi or some other protocol, including the Nest Learning Thermostat and many popular door locks. Others come with a hub that facilitates communication out to the world.
Most people have hubs without thinking twice about them: An Amazon smart speaker or a Google Nest hubs or the Apple HomePod, which allow you to use voice assistants to speak to your devices. This is handy, but of course, you can likely only use the one assistant. Hubs are necessary.
Matter: The Station supports Matter fully and acts as a hub.
Thread: An IoT communication standard and a key part of Matter. The Station embraces it.
Z-Wave: The OG smart home communication standard. Unsupported. Yep.
Zigbee: The other big IoT standard, Zigbee is fully supported.
SmartThings: Samsung’s own smart home tech, supported completely, of course.
I’ve got two other hubs in my home, one for the SimpliSafe home security system and a second for my EufyCam 2 security cams (the best home security camera system on the market). That’s right, I have two different security systems with two different hubs that speak different languages. And neither of them works well with Google. And neither speaks Matter, for that matter.
This, in a nutshell, is the challenge of today’s smart home: too many hubs, too many standards, too much confusion. And into this space steps … another hub. I’m sorry too. Don’t blame me.
Hubs function essentially as a bridge to the outside world. Think of the Matter standard as the language your devices speak, regardless of whether they’re talking on the phone or DMing or on FaceTime, metaphorically speaking. Hubs allow that conversation to reach outside of your house, so you can use your devices from anywhere in the world, via the SmartThings app. As I said, it's a necessary thing.
SmartThings Station review: performance
Yes, the Samsung Station is a hub for Matter, but it’s also a charger, and a darn good one, supporting “super-fast” wireless charging on Samsung phones. My Samsung Galaxy S22 acknowledged the Station and the 15 watts of juice it supplied with a grin and smile. Other devices won’t support those speeds, but they should charge at regular wireless speeds -- that is to say, slowly. And as with all charging thingies, you’ll have to position your phone just right or you’ll wake up with 22% battery life, as I did this morning. Sigh.
The Station can locate your devices as well through a service called SmartThings Find, which is useful in the morning when you’re scrambling to find keys or that cell phone that’s walked off. Swipe between devices on the app, then press the tile's button to locate them. You can also activate this feature through a physical button on the Station itself, which otherwise didn’t feel super handy to me.

Setting up the Station is a snap. Download the Samsung SmartThings app on either Android or iOS, plug the device in and your phone will automatically find it. If not, just tap the small plus sign to start things rolling. Voila. Next up, connect your smart home devices, and if you’ve already got SmartThings set up, you’re way ahead of the game. If not, it’s simple enough to add gear to Samsung’s app.
Matter is intended to smooth out this process, so to test it out, I screwed a Nanoleaf Essentials Matter Smart Bulb (model N67) into a kitchen light. The N67 is a brand new smart bulb that can change colors and temperatures thanks to the Nanoleaf app.
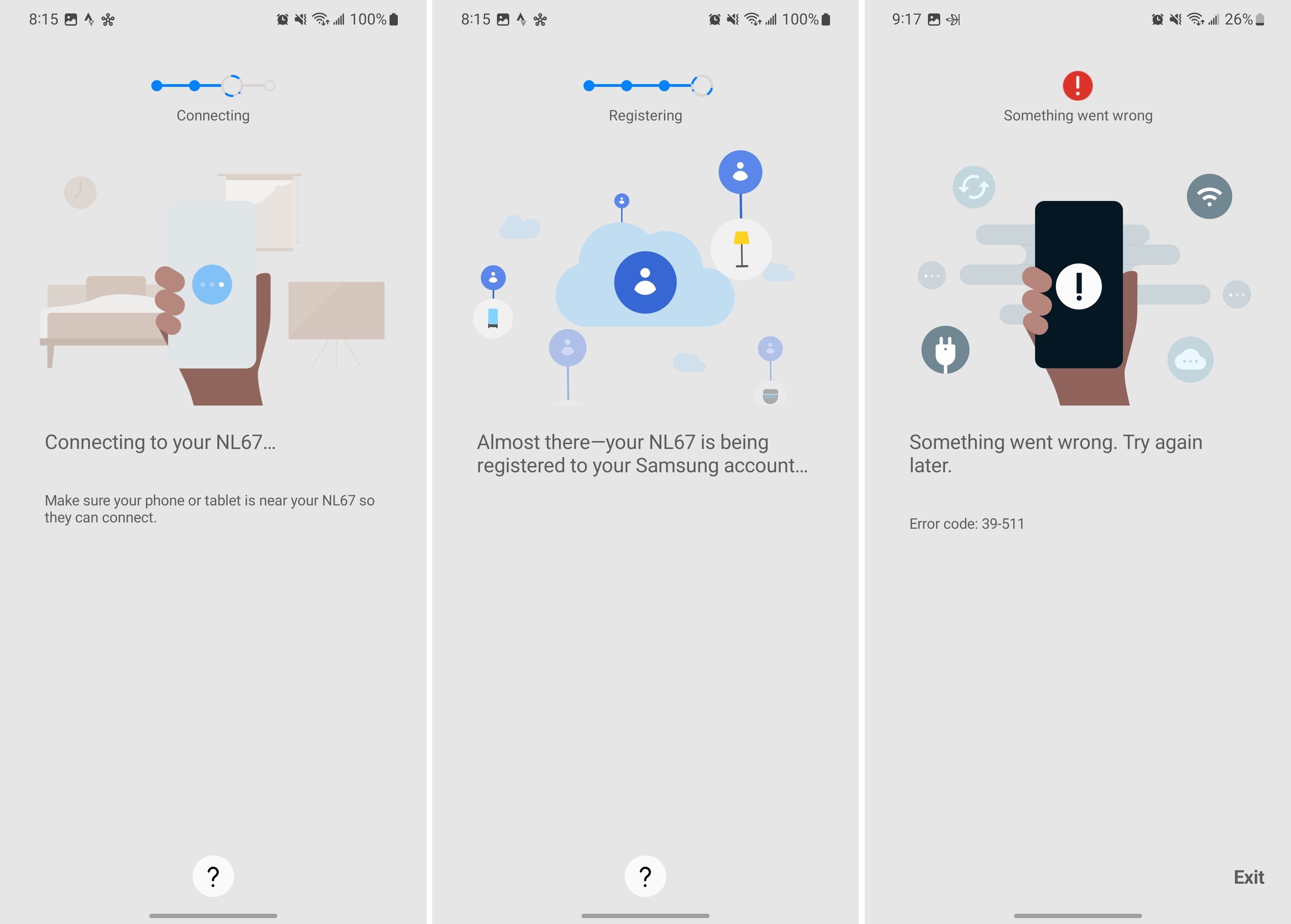
I added the N67 first to the Nanoleaf app. Once there, the SmartThings app detected the device and began registering it to my Samsung account. It … well, didn’t work. The app hung for several minutes before telling me “Something went wrong. Error code 39-511.” It did this twice in a row before I gave up in frustration.
Several days later, new firmware was pushed to the bulb, updating it from 3.2.0 to 3.5.0. Following the update, I noticed that the bulb was available in SmartThings. Had it always been there? What was the error? Is it registered to my Samsung account? What does that even mean? Regardless, once over the hump I could control the bulb flawlessly from either app. By clicking the “Share with other services” menu in SmartThings, I was able to share the bulb and its features to my Google Nest Hub, which is also a Matter hub. This worked remarkably well, but I don’t expect anyone to ever take advantage of it. Who has two Matter hubs?
Setting up Routines
The real power of connected devices lies in automation -- tying together multiple devices to change the setting, set the mood, or whatever. And frankly, I remain shocked that modern office buildings don’t do more in this regard. If you’re like me, you walk into conference rooms on a daily basis carrying both a smartphone and a laptop; Why those devices don’t interact with the room itself is beyond me. Can’t they automatically log into a Zoom room or Google Hangout, turn on the lights, enable the camera (and point it at me), and log into whatever conference is configured to start? Or set the conference room status to “occupied” or “lunchtime beer tasting” or something?
But forget the office: SmartThings Station can do that for your home, tied to the time of day, home status, or several other variables that make this a very powerful feature. Drop a phone on it to charge and you can automatically trigger a routine -- turn the music to something innocuous, set the lights to mellow yellow, whatever.
Through SmartThings, I set a routine to trigger after 10pm if I set my phone on the charger for more than 1 minute. Under those specific circumstances, the routine turned off the lights and set things to away mode. It was handy indeed, and I could see this being quite useful.
Performance score: 3 out of 5
Should you buy the SmartThings Station?
Buy it if ...
Don't buy it if ...
SmartThings Station review: also consider
This is a pretty unique proposition from Samsung but if you wish to create an ecosystem with smart devices, or need a new phone to charge on the SmartThings Station here are a couple of products to consider...
How I tested the Samsung SmartThings Station
I spent a month with the SmartThings Station to ensure that I understood the Matter ecosystem and how it worked. Testing the phone charger simply as a charger -- including the Find My Device features and so on -- was straightforward enough with my Galaxy S22 Ultra, but that's really only half of the product.
My New York City apartment lacks the cornucopia of smart home devices that suburban dwellers use, however, such as connected doorbells and security systems. So I focused my testing on the brand new Nanoleaf Essentials Matter Smart Bulb (model N67). I tested the pair over the span of two weeks, unplugging the Station, adding the Bulb to my other Matter hub, and experimenting with Routines. The more energy you invest in this feature, the more value you'll get from your purchase. But that kind of flies in the face of Matter's plug-and-play attitude, doesn't it?
First reviewed April 2023
Read more about how we test