Notability review
Notability is a note-taking app from Ginger Labs that was launched back in 2010. It’s available for iOS but not on Android. Upon installing the app, a seven-day free trial is offered, so I was able to test out the premium features for free. Some other note-taking apps offer longer trial periods, so seven days felt a little short for me, as I like to make sure that an app is compatible with the way I work before committing to pay a subscription, but it may well be plenty of time for others.
Notability Starter
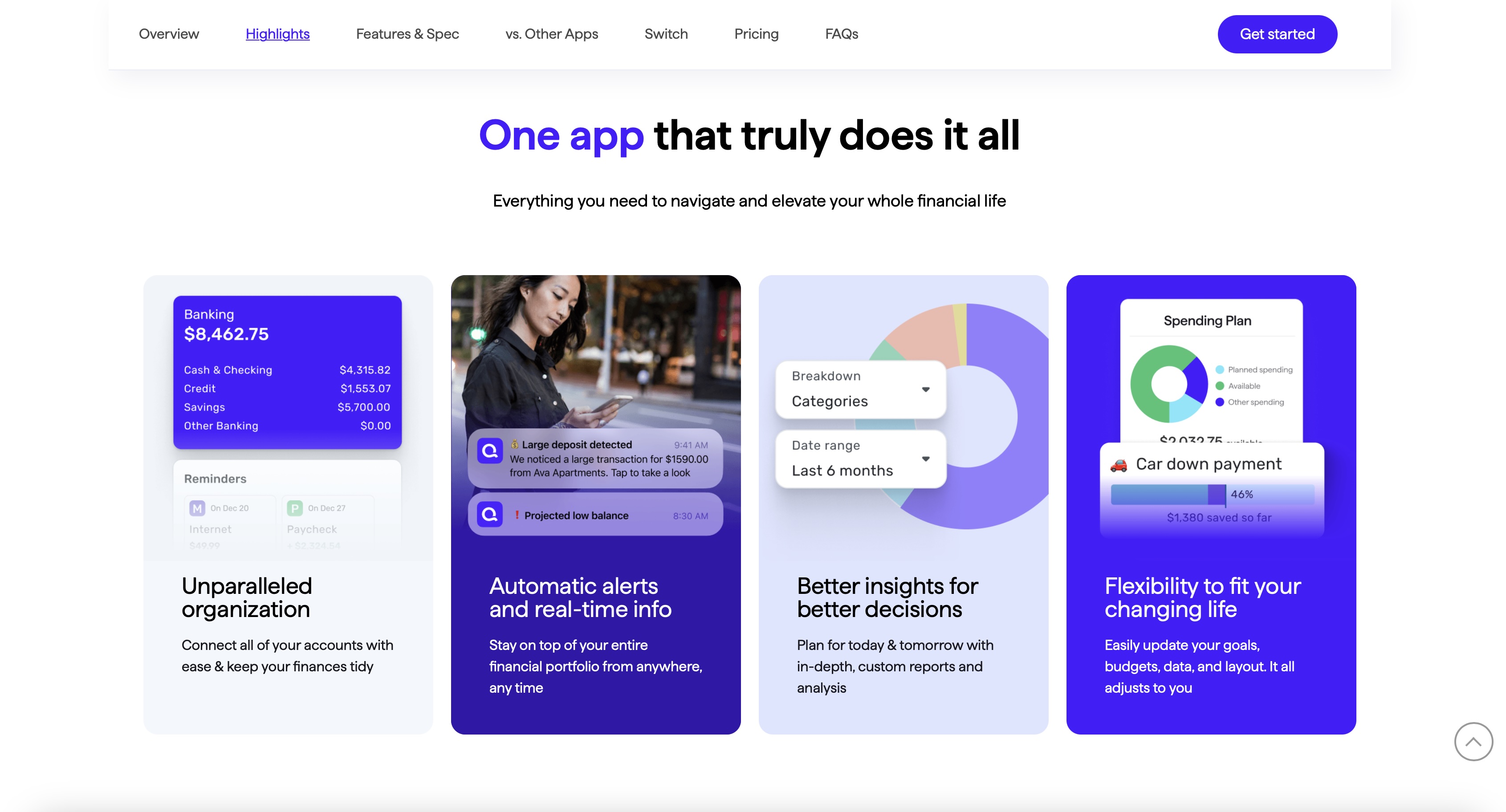
Without a paid subscription, you can create multi-media notes with a limited number of edits, import and annotate PDF documents, sync audio recordings to your notes, access the Gallery and its templates, scan documents, make use of presentation mode, view notes side by side, plus access free stickers, themes, and other content.
Price: Free
Notability Lite
For those who don't need the full suite of features, a Lite subscription provides everything in Notability Starter, along with unlimited edits, iCloud syncing across devices, and auto-backup.
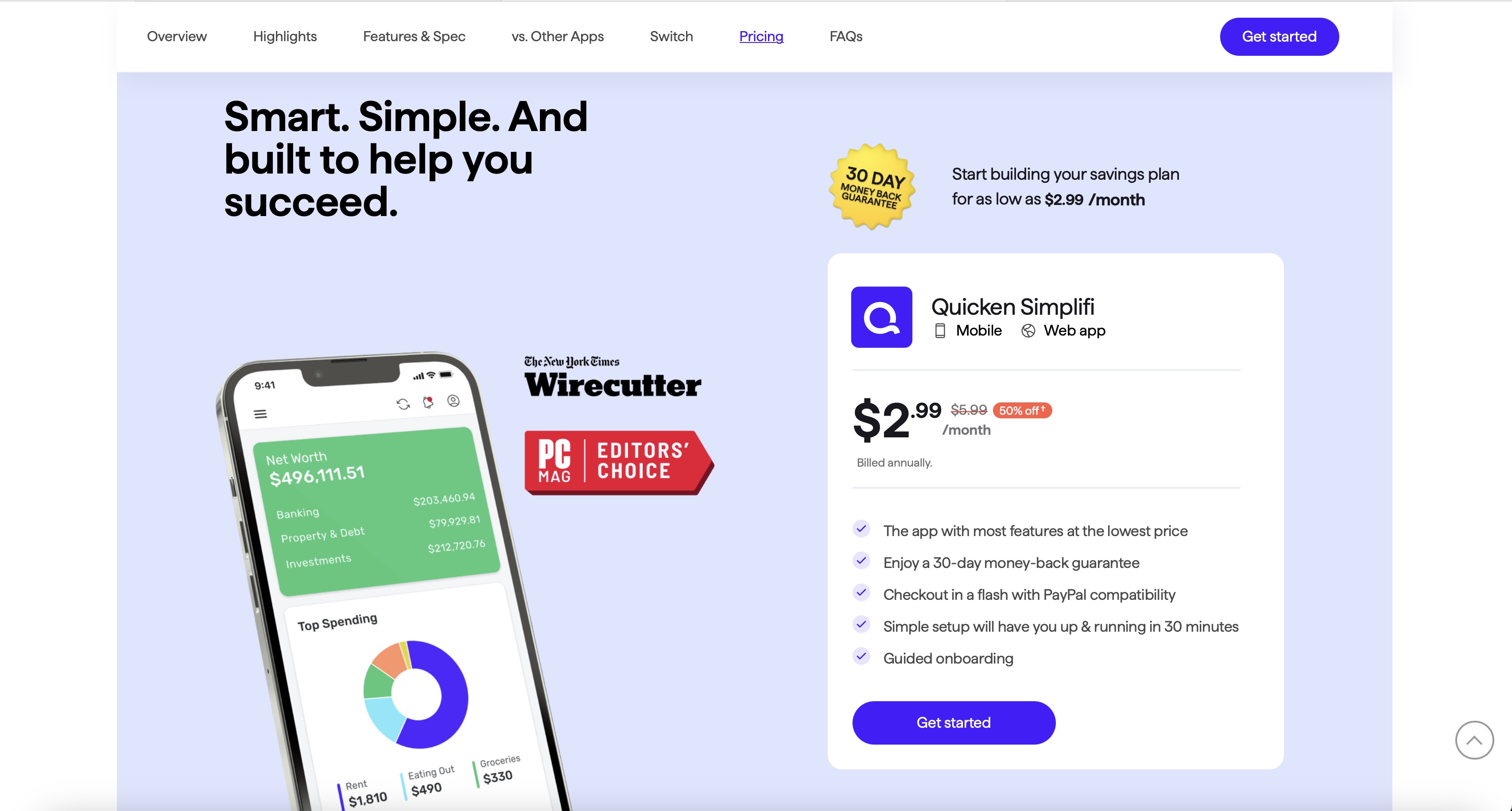
Price: $17.99 / £12.99 per year
Notability Plus
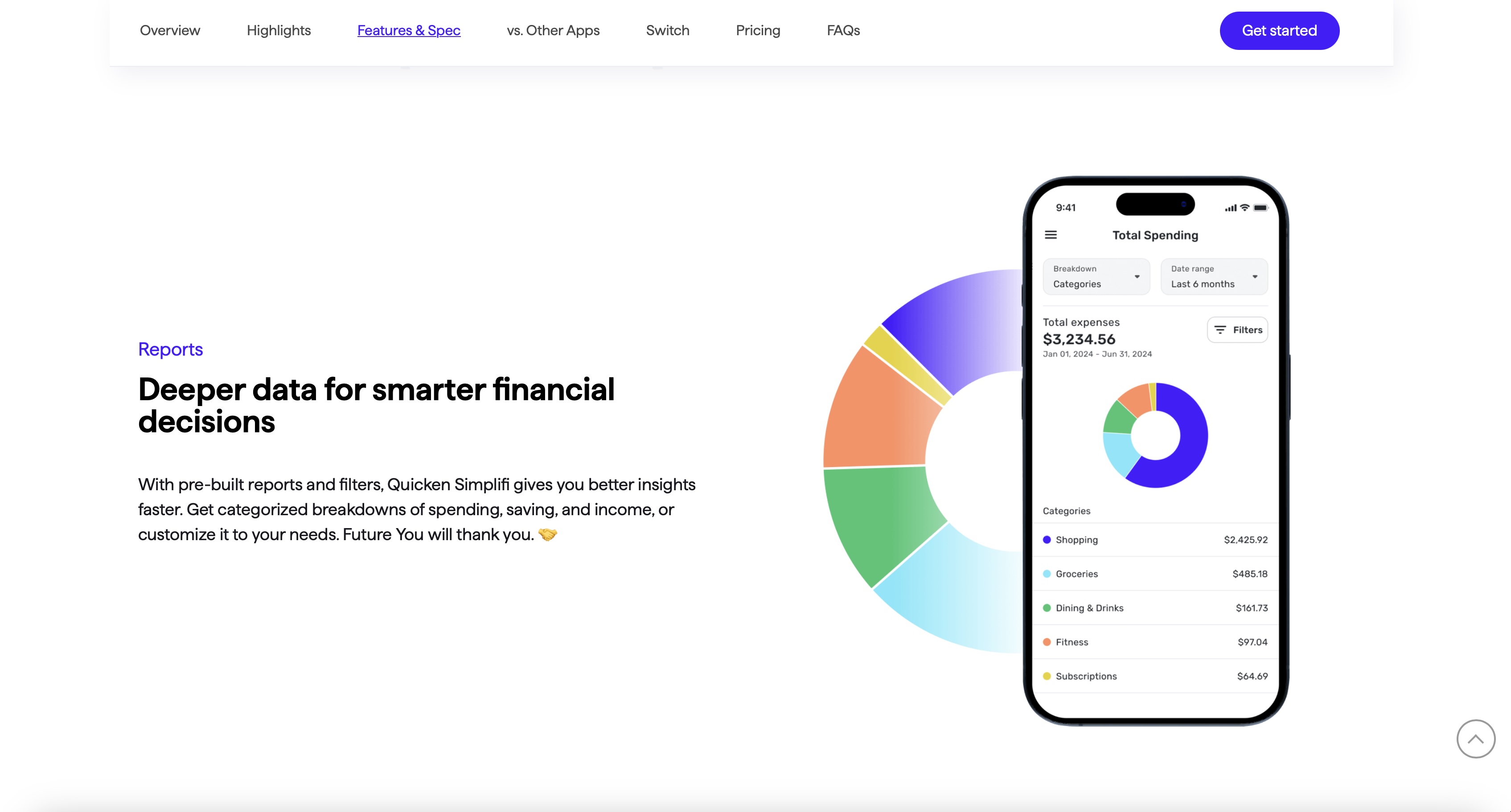
Includes all of the benefits of Notability Starter, but notes and edits are unlimited, you can convert handwriting and math equations into text, use search to locate specific entries in written notes, sync to iCloud, plus your notes can be automatically backed up.
Price: $24.99 / £17.99 per year
A limited version of Notability is available for free, offering only a set number of edits, but more features can be accessed with a subscription to Notability Lite, and full access to all features with a subscription to Notability Plus. Prices vary depending on region, but in the US and the UK, a subscription to Notability Lite costs around $17.99 / £12.99 per year, and a Notability Plus subscription costs $24.99 / £17.99 per year, a similar price to many of the apps listed in our selection of the best note-taking apps, at the time of writing.
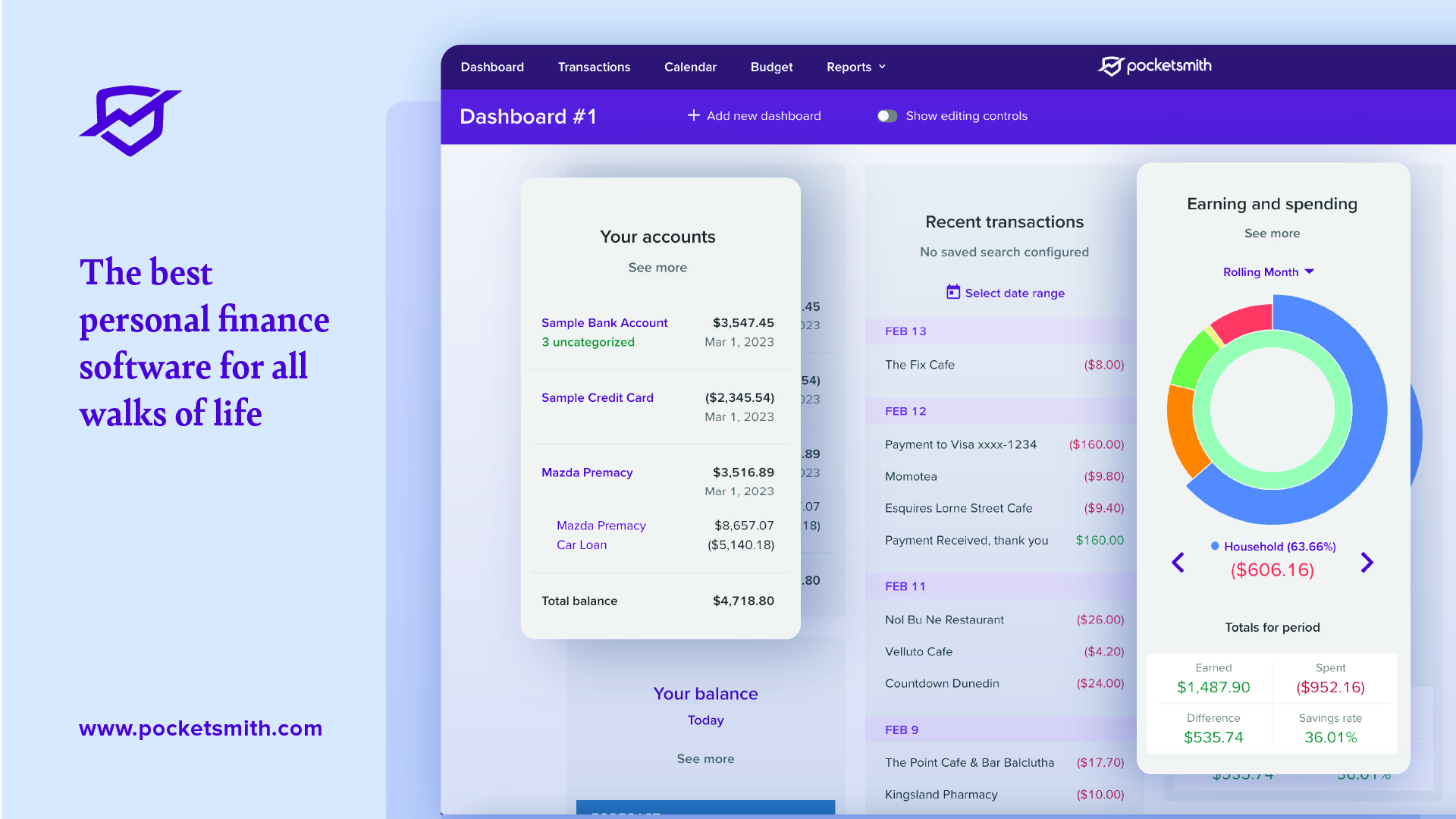
When it came to features, there were no complicated tools or settings menus. The handwriting-to-text and math equation features worked really well, even when tasked with converting my untidy scrawlings. There were two handy notes available to me detailing how to get started and the tools available to me.
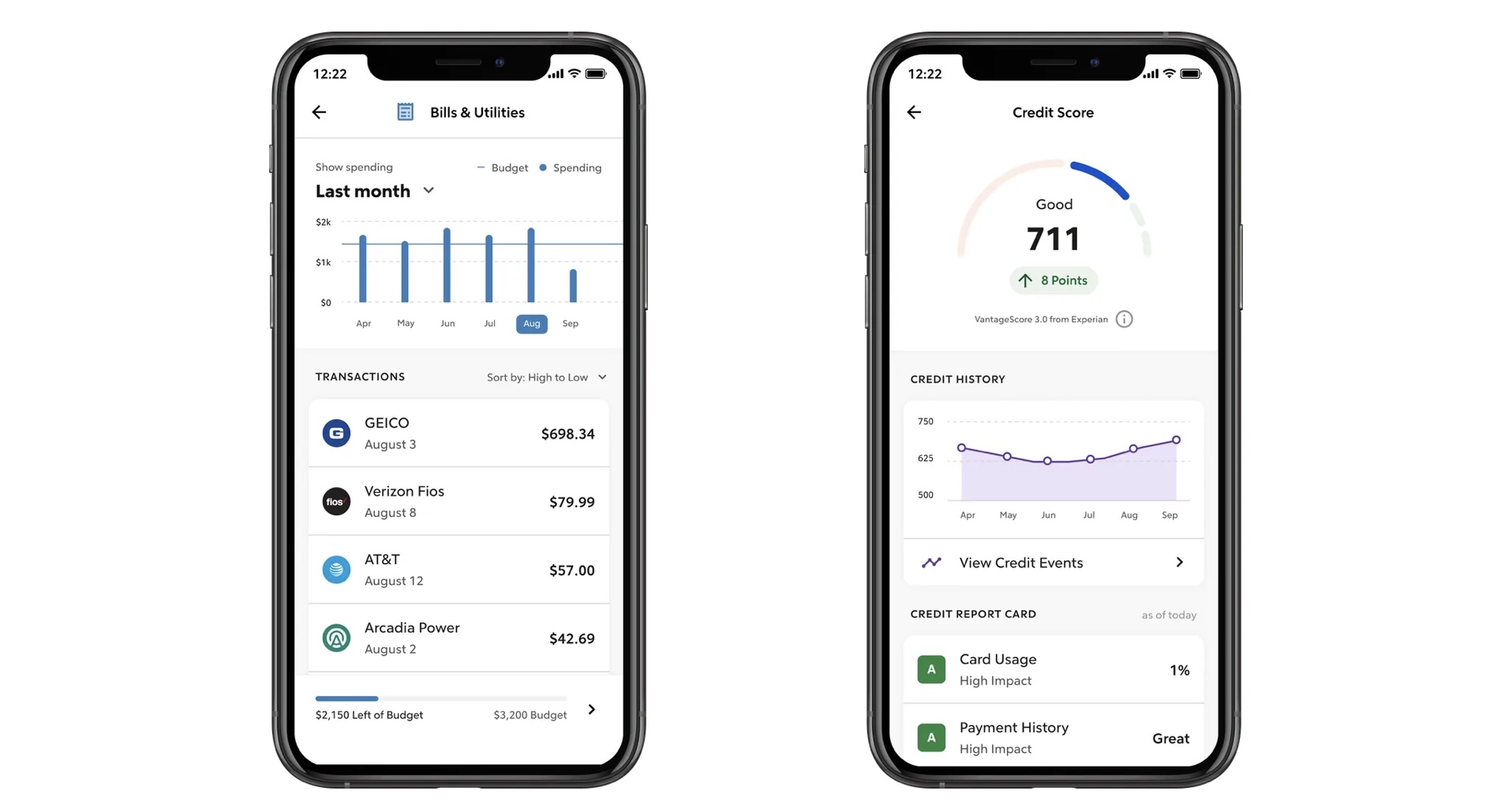
It was easy to sync my notes between my Apple devices by popping into settings and enabling iCloud Syncing, so I could view, edit, or delete my notes from any of my devices effortlessly. In order to share my notes with others, I had to go into Manage Accounts via the settings and log in to my Notability account. Doing this also meant that I could have my notes in the gallery – for example if I’d made a template that others might want to use – and meant I could follow other publishers too.
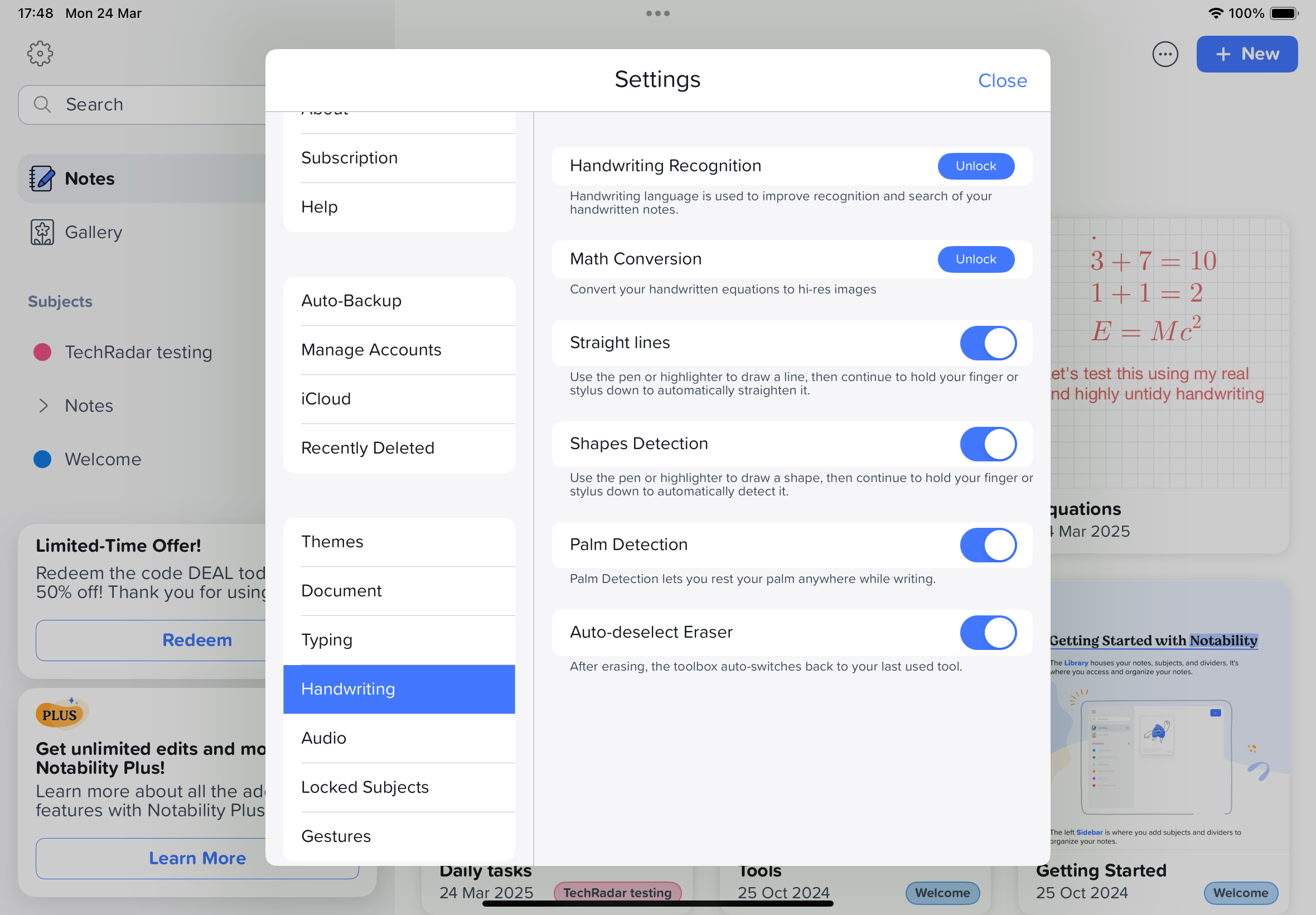
The app could be used by professionals, but only for note-taking and to share work with others, as it’s not the ideal app for collaboration. It’s a pretty nifty app for personal use, however, with plenty of free planner and to-do list templates that helped me get organized, not to mention the huge variety of colorful stickers available that made it super easy to jazz up my pages or help to add a visual cue next to certain entries.
This plethora of free stickers plus the easy-to-use tools made it easy for me to create bullet journals and planner spreads from scratch. One tool that worked well but proved frustrating was the eraser, which, for some reason, is set to revert to the previous tool I used once I'd lifted my Apple Pencil from the screen.
Although the large variety of templates supplied by Notability was a big plus, it was a shame that the templates I tried were applied to all pages within my note, so if I found I couldn’t swipe through the pages and apply a different template to each page. This would be fine if I wanted several pages of to-do lists or shopping lists, but was disappointing when my aim was to create a planner for my week with notes, lists, and goals.
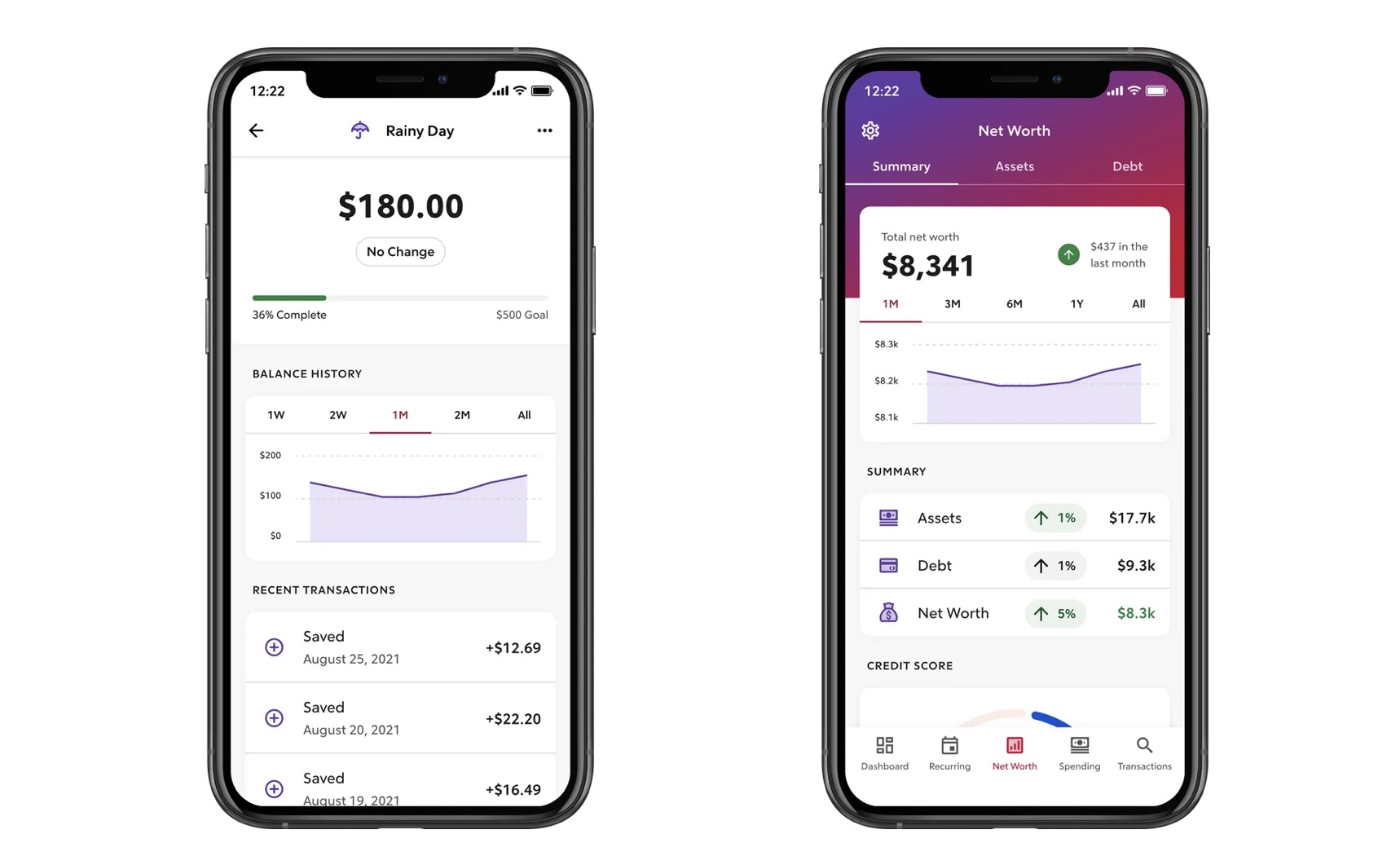
It only took a couple of taps to share notes as a PDF document via channels like email, and social media messaging, by clicking on the options button from within my note. There was also another option to select allowing me to customize the format, including PDF, Note, JPEG, and PNG file types. I could also decide which pages I wanted to send, as well as if I wanted to include the background paper, add page margins, attach my audio recordings, or password-protect the document.
Sharing documents with colleagues or family members is easy to do: within the note options there are buttons to create and share a link, or stop sharing. If your intended recipient has the Notability app, it can be downloaded as a note and, if not, they can open up the document as a PDF in their browser.
As there's a button in the app to update the linked note from the source account, I assumed real-time collaboration would be possible. As it happened, however, any changes made did not sync to the downloaded note in the Notability app, but would instead update the PDF, which would need to be redownloaded to have the up-to-date note available. This way of working still has its uses, of course, but real-time collaboration would have been more efficient.
In summary, this isn't an appropriate app for streamlined collaborating. But it's very simple to get started with Notability, and there are enough tools and free content to help organize and keep track of projects or personal goals, making this a good option for students, or anyone working solo or on personal projects.
Should I buy Notability
Buy it if…
You want simplicity
If you want a straightforward note-taking app that's not boring, then Notability would be a good fit. The tools and settings are easy to master, and every element is satisfyingly uncomplicated.
You want to share documents easily
It only takes a couple of taps to share a PDF of your notes, and just a couple more to adjust the file type, page range, and more if required.
Don't buy it if…
You want to collaborate in real-time
The process to share a link to some of my notes was simple, but the linked content only updates in an uneditable document, as syncing stops when the file is downloaded, even as a Notability note. As a result, this means collaborating with colleagues would be a long-winded process.
You want to create all-in-one planners
It was very useful to have access to a broad range of templates, but it's frustrating that the template applies to every page within the note, rather than individually.
Notability review: Also consider
Evernote
At the time of writing, Evernote is rated as the best dedicated option in our selection of the best note-taking apps. You can create up to fifty notes and one notebook on one device for free, or a subscription can be paid to get access to more features, such as unlimited devices, Adobe Acrobat, 20GB of uploads per month, and features tailored specifically for team working.
How I tested the Notability app
- I used Notability for a week
- I used it to write notes, plan, and create a bullet journal
- I tested out note sharing and all of the features available
I spent a week using Notability as my main format for note-taking and for planning out my week. I also used it to create my own bullet journal.
I reviewed how straightforward it was to get started on the app, and how user-friendly and easy to navigate the interface was. I experimented with the different tools, exploring their different settings and assessing how well they performed. Finally, I tested how easy it was to share files, and how easy it would be to work collaboratively using Notability.
- First reviewed: March 2025
- Read more about how we test