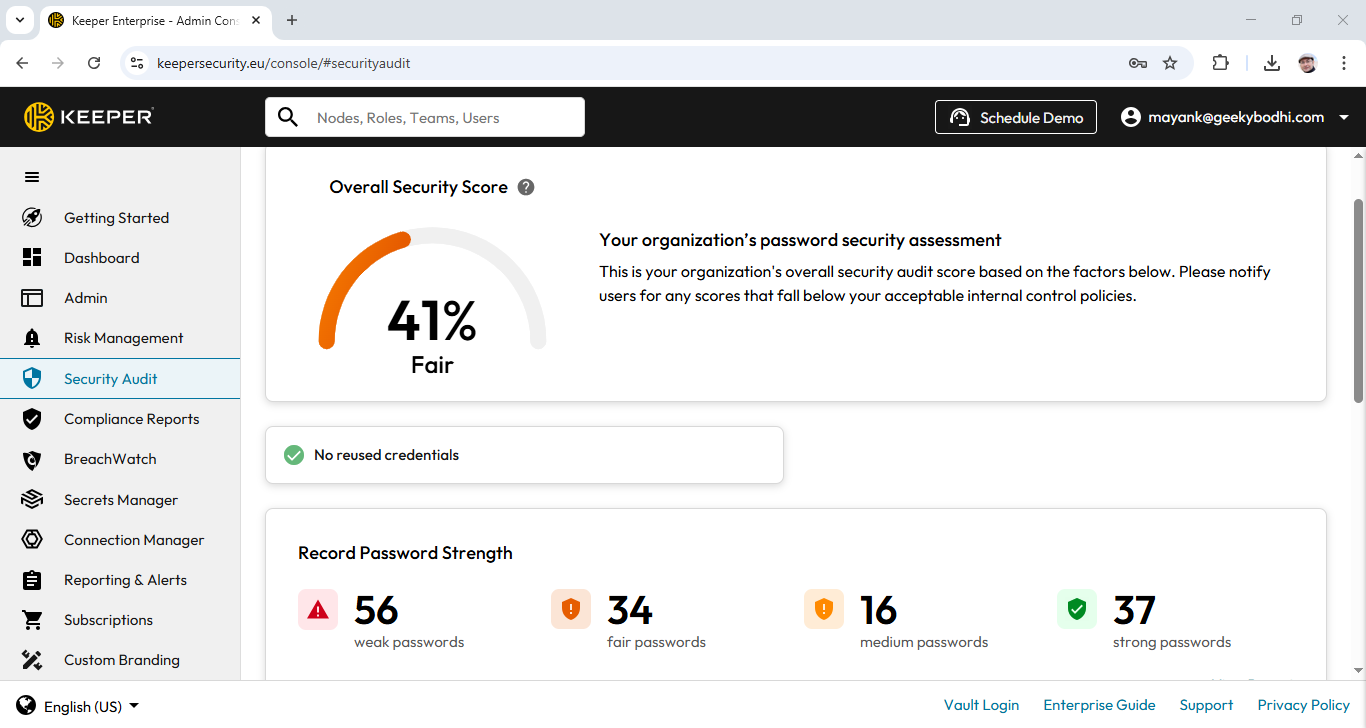
Bitdefender Antivirus Plus is a Windows malware-hunting powerhouse which includes all the antivirus basics, and also packs in more protective layers and features than many security suites. Top-notch ransomware protection, reliable tracker-blocking, effective anti-phishing, a limited 200MB a day free VPN, one of the most secure browsers around, and that’s just the start. Fair prices and excellent protection rates make this one of the best PC security tools around; keep reading and we’ll tell you exactly why.
Bitdefender Antivirus Plus: Pricing
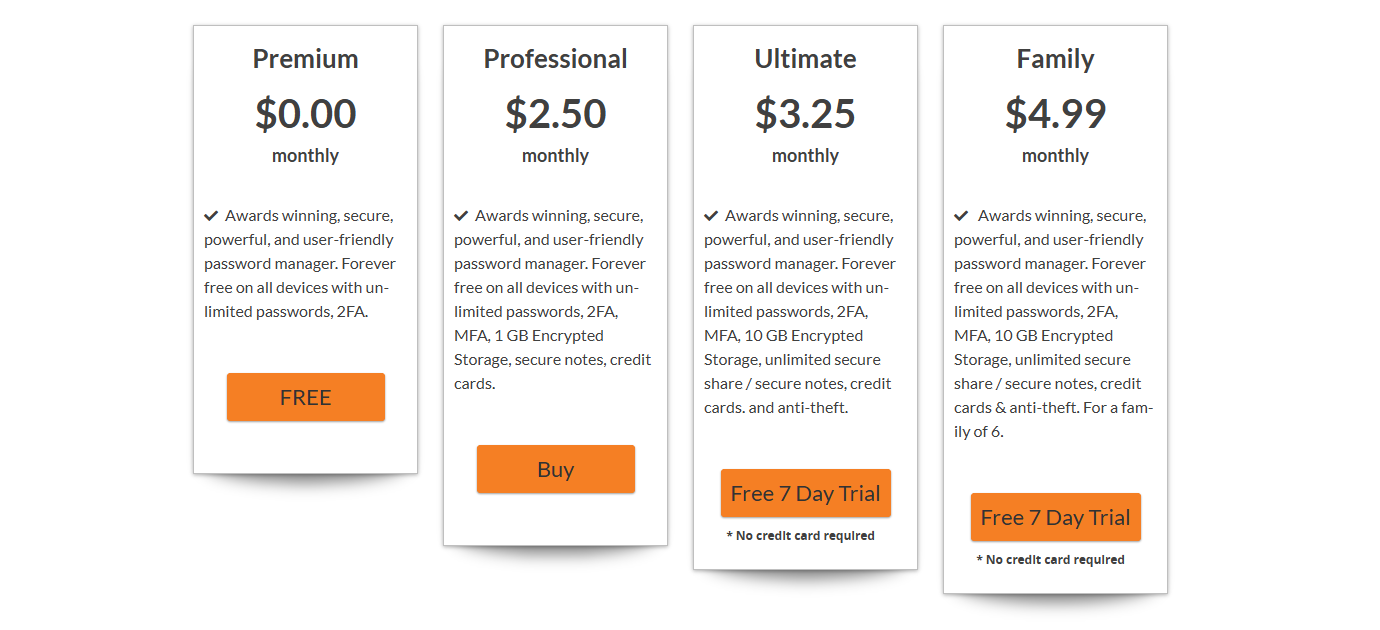
Bitdefender Antivirus Plus is the company’s lowest-priced desktop antivirus. It protects up to three Windows devices for $44.99 in year one, $59.99 on renewal. A 30-day trial gives you a chance to check out the app before you buy.
Bitdefender Internet Security (next up in the range) adds a firewall and parental control. That lifts the price to $59.99 in year one, $84.99 on renewal.
If you’ve anything other than Windows hardware to protect, Bitdefender Total Security could be a better deal. Not only does it include the firewall software and parental controls, it also throws in device optimization, and - crucially - protects any mix of up to five Mac, Android and iOS devices as well as Windows. And yet, it’s only a little more costly than Internet Security at $69.99 in year one, $99.99 on renewal.
If you’re after maximum power, Bitdefender Ultimate Security includes absolutely everything: antivirus and security functionality for up to ten devices, a full and unlimited VPN, and a complete identity theft protection package with up to $2 million insurance. The price is much higher at $119.99 in year one, and $239.99 on renewal. But the full VPN alone has a lot of value. Sign up for even the most basic NordVPN package and you’ll pay $68.85 in year one, $112.35 on renewal.
These are fair prices, but depending on the mix of features you need, there could be better deals around. Avast One’s cheapest paid plan, Avast One Silver, protects all platforms, has a more generous free VPN (5GB data a week vs. 200MB), includes a firewall and blocks webcam hijacking, but it’s only $35.88 in year one, $79.99 on renewal.
The Norton antivirus range is another one worth a look. Norton 360 Standard covers up to three mobiles or desktops, has antivirus, a full VPN, 2GB cloud backup and a password manager, but is priced at only $39.99 in year one, $94.99 on renewal.
Bitdefender Antivirus Plus: Easy to use
If you’re looking for an antivirus you can install and forget, Bitdefender Antivirus Plus has a lot of appeal. The app installed easily for us, then moved to the background and made most of its decisions entirely automatically, keeping any technical hassles to a minimum.
Other providers often have a very different user experience. Present Avast One with an app it doesn’t recognize, for instance, and it’ll launch a scan and leave you waiting for up to 15-20 seconds before you can continue. By comparison, Bitdefender might ask if you trust the app, but mostly it sorts out the issue for itself.
Try Avira antivirus and you’ll get notified with pop-up alerts for every threat, which can become annoying (a malicious web page opens lots of dangerous links, for instance.) Bitdefender displays the first alert, but doesn’t bother you with the rest. The information is still available in a Notifications page, but you don’t have to look at it unless you’re interested.
Bitdefender Antivirus Plus: Interface
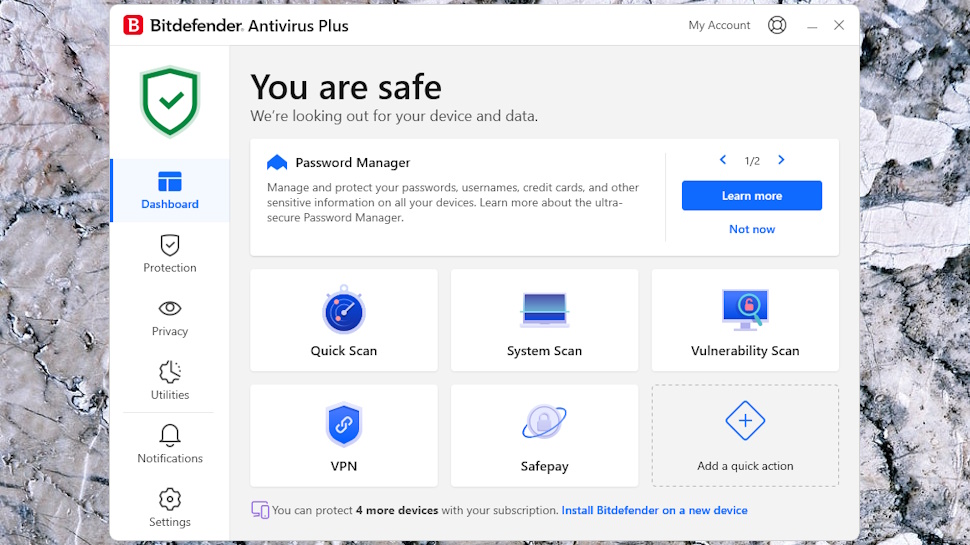
Bitdefender Antivirus Plus opens with a simple dashboard offering one-click access to its most useful features: quick scan, system scan, the VPN and the secure browser, Safepay.
In theory you can customize the dashboard with your own shortcuts. But in practice, there are only two other items you can add, in the Password Manager (only a trial) and the Data Shredder. The dashboard would benefit from more flexibility, such as the ability to pin your own custom scans (more on those below.)
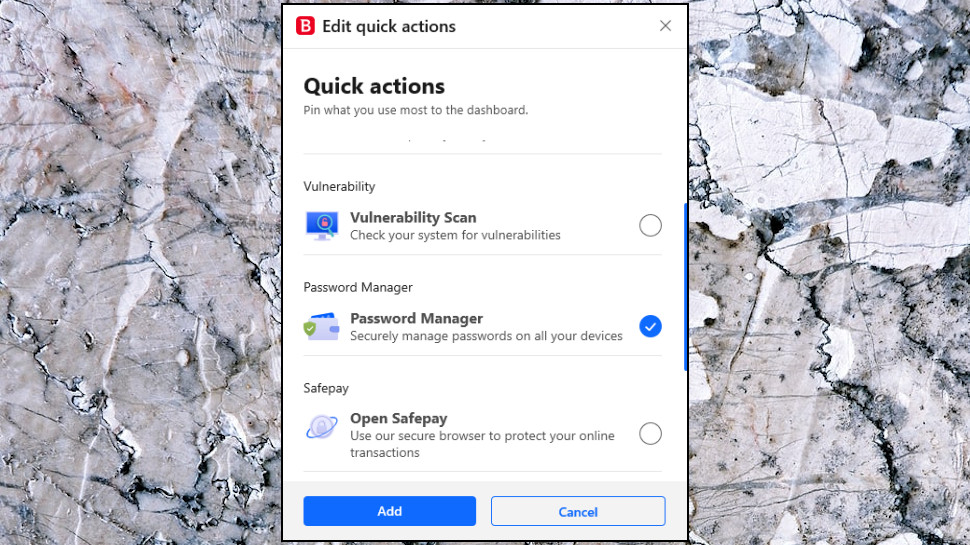
There are plenty of other tools and options available, and Bitdefender organizes those with icons in a left-hand sidebar: Protection, Privacy, Utilities, Notifications, Settings. If you need to control the Anti-Tracker, for instance, click Privacy, and you can edit its settings, or turn it on and off with a click.
Bitdefender’s Explorer integration gives you an easy way to access features without launching the full dashboard. Just choose your preferred files, folders or drivers, and you can scan (or securely delete) them directly from Explorer’s right-click menu.
Bitdefender hasn’t changed the core of its interface for a very long time. That’s a pity, because as we’ve discussed, there is room for improvement. But at its heart the interface is generally easy to use, and it’s likely you’ll find the functions and features you need without any difficulty.
Bitdefender Antivirus Plus: Antivirus Scanning
Bitdefender offers a strong range of scan types covering all kinds of situations.
Quick Scan runs a brief check which inspects the most commonly-infected areas only. This took a reasonably short 8:14 on our test system, falling just a little to 7:36 on the second scan.
System Scan is a deeper analysis which crawls your entire storage device and explores everything it finds. That takes much longer for the first scan, but drops hugely afterwards as Bitdefender only scans new or changed files.
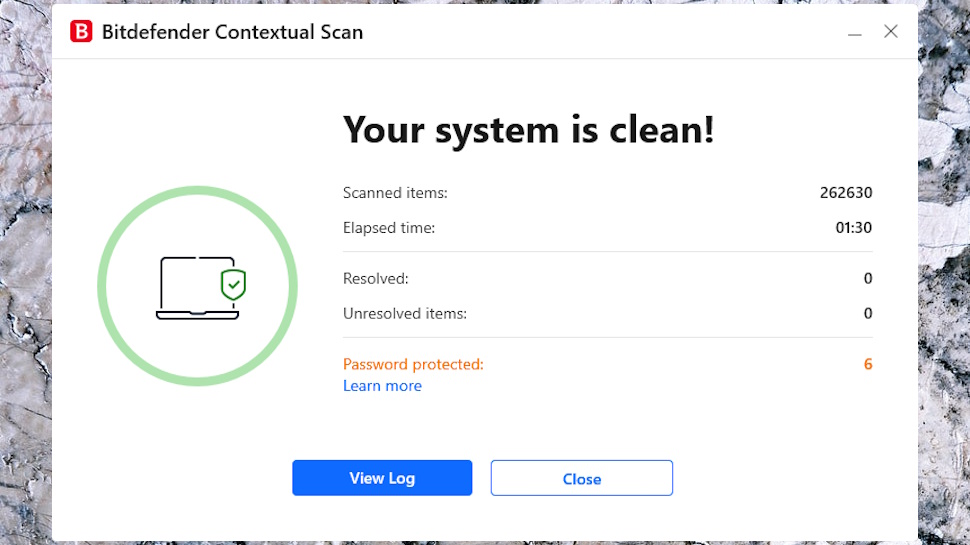
To test this, we scanned 50GB of application files. The first run took 37:44, a little behind Avast (35:40) and Norton (32:01.) The story changes on subsequent scans, though, with Avast taking 34:53, Norton falling to 3:48, but Bitdefender completing in just 90 seconds.
Rescue Environment is a bootable scanner which lives on your hard drive and removes even the most stubborn of threats. Just launch it from the dashboard, reboot when you’re prompted, and Rescue Environment hunts down and removes any threats. It’s a great tool and the ability to launch it from your Bitdefender app is a major usability plus (Avira and many other vendors expect you to download, set up and run their boot scanners separately.)
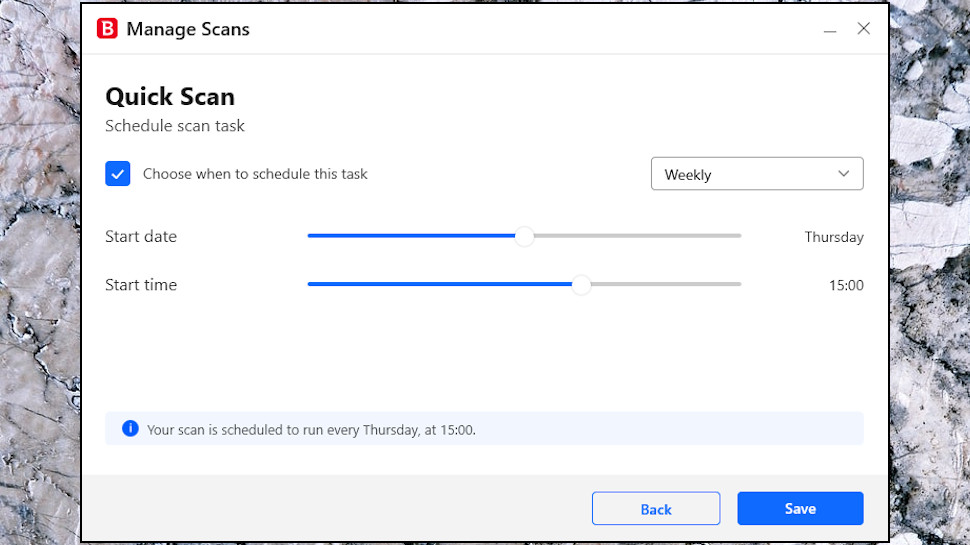
A scheduler allows you to run scans automatically. That’s good news, though it’s not as flexible as some of the competition. Avast allows you to choose which days of the week need a scan (Monday, Wednesday and Friday, say); Bitdefender can run as a scan every day, or the same day every week, but that’s it.
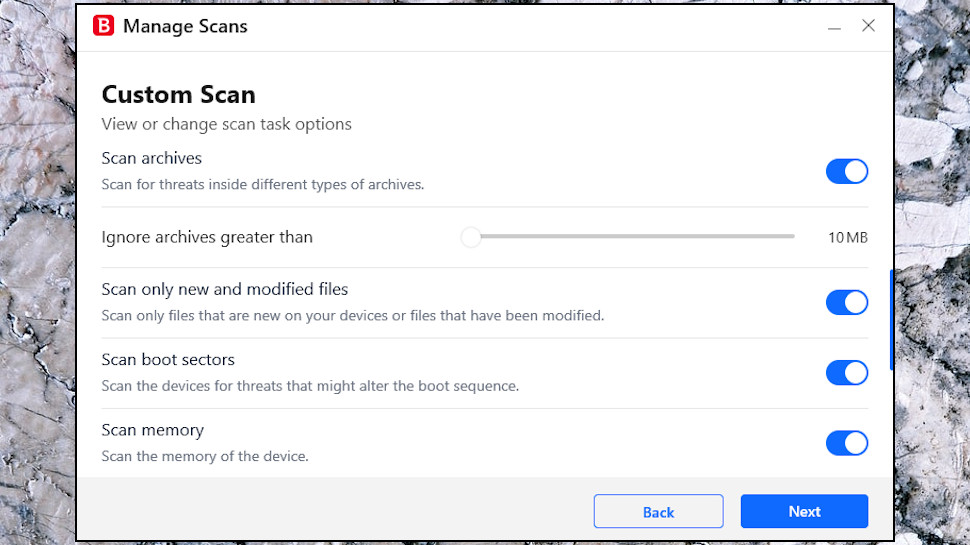
On the plus side, Bitdefender has an excellent Custom Scan feature which allows you to create new scan types for different situations. Looking for speed? You could create something which checked running processes, RAM and the Registry only. Maybe you’re worried about the contents of your Downloads folder? A custom scan could check that location only, maybe scan larger archives than usual (regular scanning ignores zips larger than 10MB) to be sure of catching any threats.
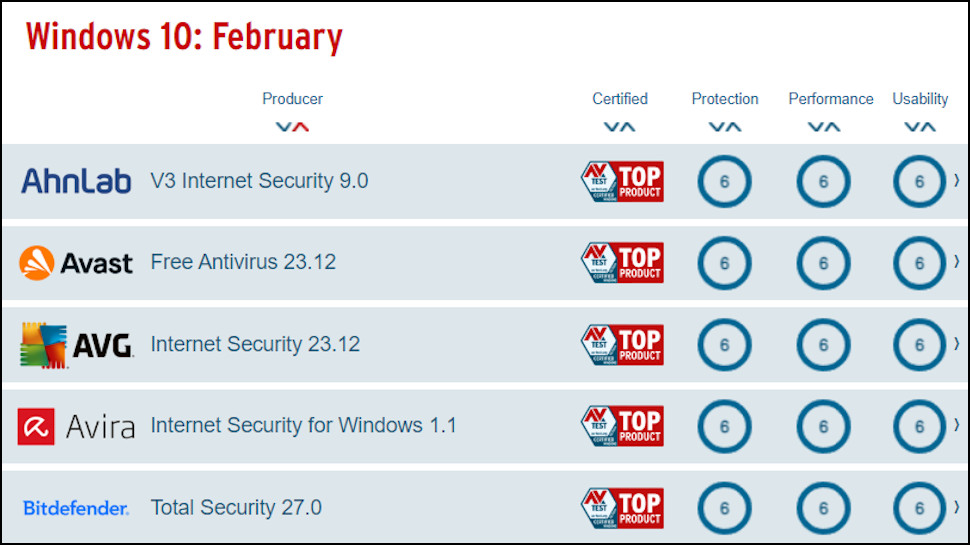
Bitdefender Antivirus Plus: Antivirus Lab Test Results
Although we put every antivirus app we review through our own series of tests, we also pay close attention to results from the big antivirus testing labs.
We follow nine tests from labs including AV-Comparatives (Real-World Protection, Malware Protection, Android, Anti-Phishing, Performance), AV-Test (Windows, Android), MRG Effitas (360° Protection Testing) and SE Labs (Endpoint Security Home).
Each test has its own scoring system, making it tricky to compare performance. To address this, we use a special algorithm which (as long as an app is in at least five tests) converts the various results into a single summary score from zero to 10 representing the vendor’s overall rating.
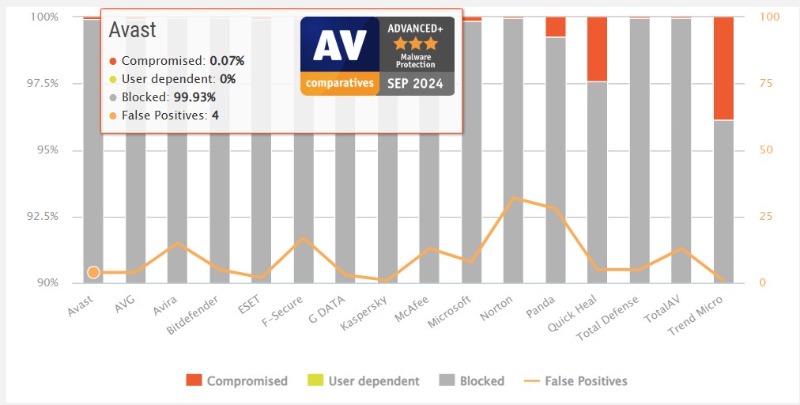
Bitdefender appears in the latest reports for eight out of our nine core tests, making this a strong all-round test of its abilities. And Bitdefender’s combined score was excellent at 9.97, earning it second place just behind Avast’s 9.98.
Looking at the individual tests, Bitdefender’s most significant weak spot was an 11th place in the Malware Protection test. But that doesn’t represent a huge difference in results; Bitdefender achieved a very creditable 99.92% protection rate, and it just happened that the top-rated Norton and F-Secure managed 99.97%.
Results can vary month to month, though (Bitdefender topped the previous Malware Protection test), and the company scores very highly elsewhere. Bitdefender tops the anti-phishing charts, for example, blocked 100% of Android threats, and scored full marks in the latest MRG Effitas and AV-Test Windows reports.
Overall, the lab test results are very positive for Bitdefender, showing above average performance in most areas, and market-leading results in many. If you’re looking for reliable protection across the board, Bitdefender delivers.
Bitdefender Antivirus Plus: Anti-Ransomware
Defeating ransomware isn’t just about spotting known threats as they’re downloaded. A good antivirus needs multiple other layers of protection, such as using behavior monitoring to detect even brand new threats before they can do any harm.
We test an antivirus’ ransomware-fighting abilities by pitting the app against our own simple ransomware simulator. This has never been publicly released, ensuring that an antivirus can only detect it by picking up on its suspicious behavior (spidering through test files and opening each one in turn.)
Previously we’ve managed to bypass Bitdefender’s protection for just a few seconds, but not this time. Bitdefender killed our simulator almost immediately, before it could damage a single file.
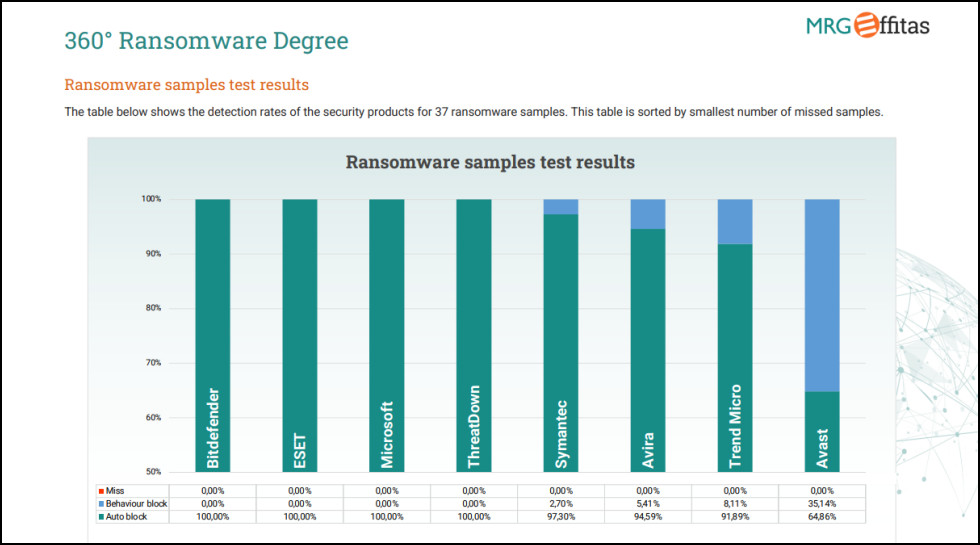
Even if some of your files are damaged, that’s not the end of the story. Bitdefender’s Ransomware Remediation can automatically protect ransomware-encrypted files, recovering them once the infection was removed. The technology has worked faultlessly in previous reviews, giving Bitdefender a major advantage over other security vendors.
To confirm our results, we took a look at the latest MRG Effitas Ransomware tests. This tested the performance of Avast, Avira, Bitdefender, ESET, Microsoft, Norton, ThreatDown and Trend Micro when faced with 37 ransomware samples. Bitdefender, ESET, Microsoft and ThreatDown came equal first by automatically blocking every threat, without needing to use their behavior-monitoring layer. That’s another great result, and suggests Bitdefender is one of the best vendors around for battling ransomware.
Bitdefender Antivirus Plus: Quarantine
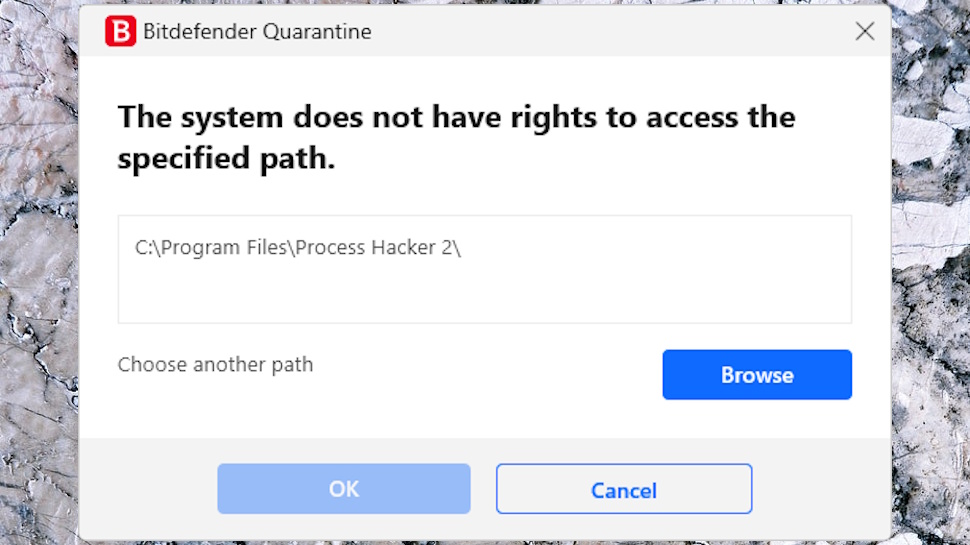
Any potential threats Bitdefender detects and removes are sent to quarantine, rather than being deleted. Quarantine is like a Recycle Bin for executables: it keeps potentially dangerous files locked away where they can’t do any harm, but, if Bitdefender accidentally removes something you’re 100% sure is safe, you can restore the file and tell Bitdefender not to touch it in future.
Although this is generally a very good idea, we noticed a problem. Bitdefender detected part of a legitimate app as a potentially unwanted threat, and moved it to quarantine. We hit the Restore button to put it back, but Bitdefender complained that ‘the system does not have rights to access the specified path.’ It had broken our app and couldn’t fix the problem.
This wasn’t a huge issue, as we were able to restore the file to our desktop and manually move it to the right location. But some users may not know how to do that, and even if you’ve no problems restoring any files, this is still a small usability hassle.
Bitdefender Antivirus Plus: Anti-phishing
The best security tools don’t just detect and block web threats as they appear: they prevent you ever reaching them in the first place. That’s why we’re always very interested in an app’s ability to keep you safe from phishing and other malicious websites.
Antiphishing doesn’t get much attention from the labs, but AV-Comparatives did run a small test on the feature last year. Bitdefender led the pack with an excellent 96% protection rate, just ahead of Avast (94%), AVG (94%), ESET (92%) and Avira (88%.)
We ran a test of our own, and attempted to access 100 brand new phishing URLs on a Bitdefender-protected system. The protection rate was identical at 96%, but Bitdefender didn’t lead the way this time. Avira topped our anti-phishing chart with 100% protection, while Avast managed 99%, and Norton scored 95%.
We also compared Bitdefender’s results with Chrome, to give us a better idea of how much extra protection it adds. The answer turned out to be a lot, as Chrome ‘only’ blocked 64% of our test URLs. These included the four URLs that Bitdefender missed, though, so if we used both Bitdefender and Chrome together, we would have received warnings about 100% of our test links.
Bitdefender Antivirus Plus: Performance Impact
We expect a quality antivirus to offer reliable and accurate malware protection, but that’s not all. The best apps deliver their protection without slowing down your device, raising endless false alarms or otherwise causing daily hassles.
AV-Comparatives’ Performance Test measures the performance impact of 16 antivirus apps on various common tasks: browsing websites, downloading files, installing and launching applications, and more. Bitdefender had a little impact on application launch times, but was still very fast overall, and received AV-Comparatives top Advanced+ award.
Our own tests showed much the same results. The excellent PCMark 10 benchmark found barely any performance impact from Bitdefender, and although our boot times lengthened a little, they’re still comparable to similar apps. Our test system took 65 seconds to fully load Windows and 81 seconds to fully load a collection of apps, for instance; Bitdefender increased this to 73 and 100 seconds, but that’s almost identical to Avast’s times of 72 and 102 seconds.
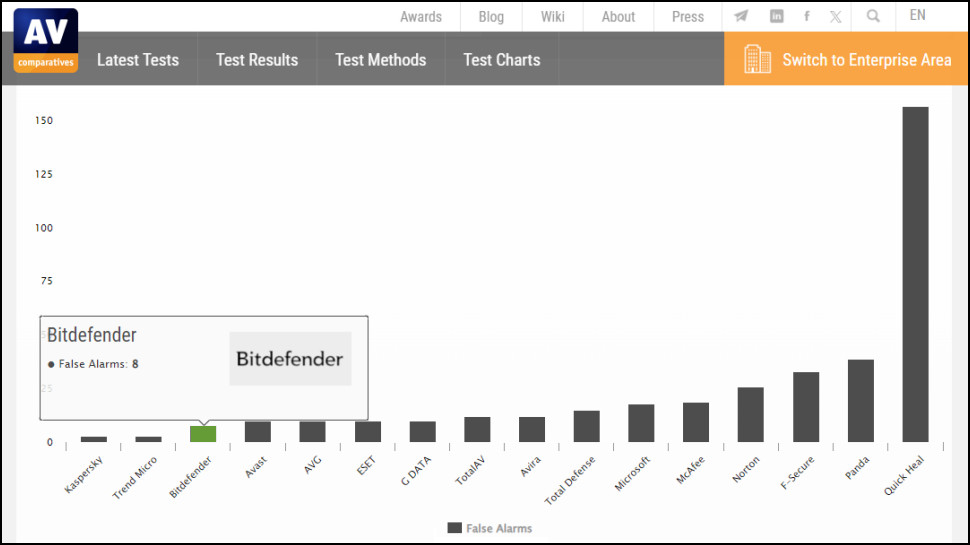
It’s a similar story with false alarms. Bitdefender has a few more than Avast in AV-Comparatives’ most recent Real-World Protection Test (3 false alarms vs. 1.5), but that’s across 512 test cases, such a marginal difference that you’re unlikely to notice.
You may have a different experience, depending on the websites that you visit and the apps you use. But our tests suggest that although Bitdefender isn’t quite the most lightweight of antivirus apps, it has less performance impact than most, and didn’t cause us any significant speed issues.
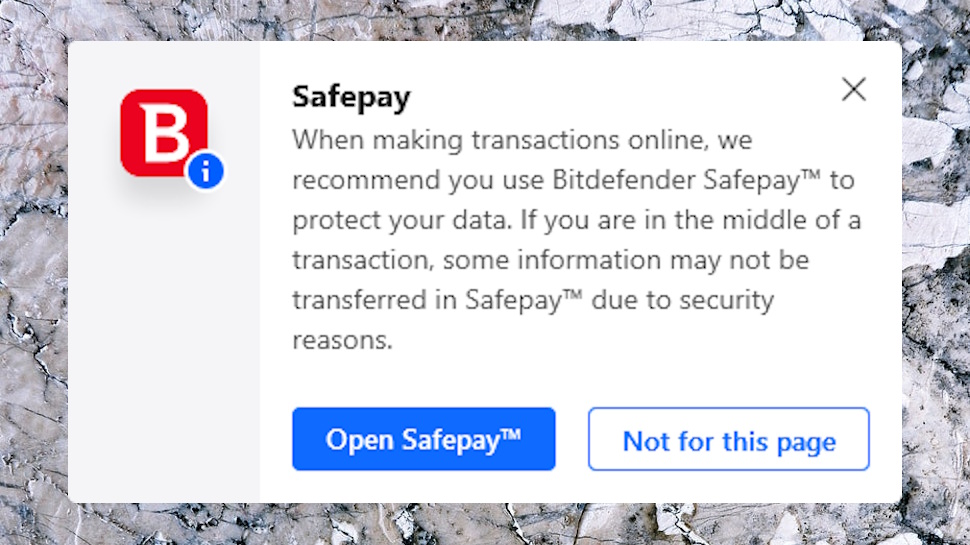
Bitdefender Antivirus Plus: Safepay
Many security vendors offer some form of ‘privacy browser’, but typically you can get much the same result by installing a few well-chosen extensions, or a third-party freebie like Brave Privacy Browser.
Bitdefender Safepay is a secure browser which protects you both from web dangers, and malware which might have smuggled itself onto your own system.
The protection starts by Bitdefender recognizing when you’re accessing a sensitive site. When we visited a banking site, for instance, an alert popped up prompting us to open the website in Safepay (it can automatically connect to the VPN, too.) Sounds like a small point, but that one idea reduces the chance that you’ll forget to turn Safepay on.
The other major Safepay plus is it runs on its own virtual Windows desktop, isolated from everything else on your system. Malware can’t capture your keystrokes or record screenshots of what you’re doing (we tried with commercial and custom tools of our own), and the virtual keyboard prevents even hardware keyloggers from recording your activities.
Put it all together and Safepay offers way more protection than other privacy browsers, making it one of the highlights of Bitdefender’s range.
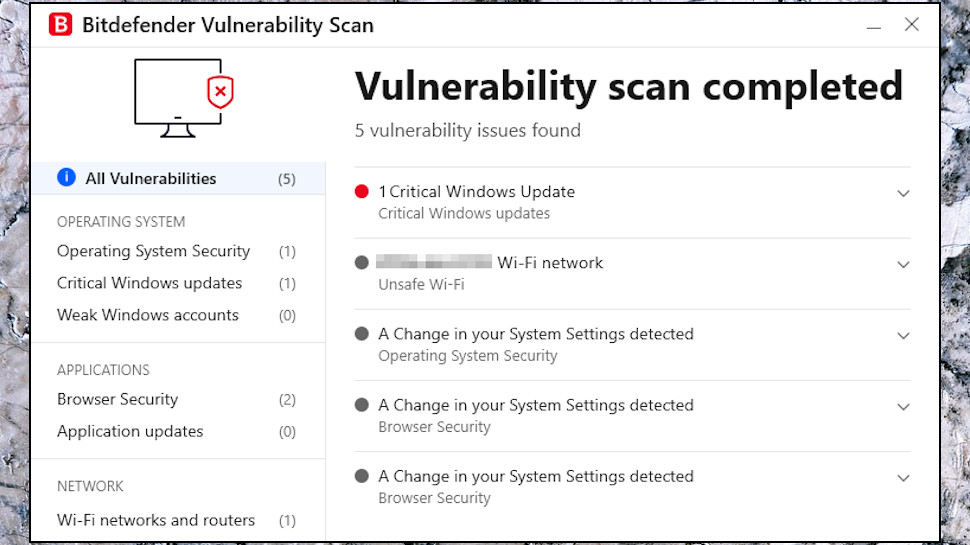
Bitdefender Antivirus Plus: Vulnerability Scan
Bitdefender’s Vulnerability Scan checks your device for various issues which might make it open to attack: missing updates, weak passwords, dubious Windows and browser security settings, and more.
This kind of tool can be very useful, but Bitdefender’s offering has rarely told us anything interesting in previous reviews, and we didn’t see much improvement this time around.
The Vulnerability Scan warned that our Wi-Fi network was ‘unsafe’, for instance, because it didn’t have a password. We had intentionally set up a vulnerability, but we hadn’t removed the password; we had changed it to, well, ‘password.’ If a user doesn’t look closely, Bitdefender’s misleading description makes the real issue easy to miss. Worse, this issue has been around for years (we found apparent references to it on the Bitdefender community forum from 2017.)
The Vulnerability Scan found four low-level browser and operating system issues. That sounded interesting, but they turned out to be extremely minor, such as a setting on our system which allowed users to edit Internet Explorer security zones.
The scan didn’t find any missing application updates. It did report a missing Windows Security update which had just come out, which is good news, although we would expect any properly configured system to find and install Windows updates all on its own.
Other providers delivered more on the same system. Norton’s Software Updater found 11 missing application updates, for instance. Avast’s Smart Scan clearly warned us about our weak (not missing) Wi-Fi password, and although it ignored the Internet Explorer security zone ‘issue’, did make some more useful suggestions, including turning on Data Execution Prevention (a valuable Windows exploit protection technology) and ensuring device notifications weren’t displayed on the lock screen.
The Vulnerability Scan still has a little value. Malware often changes system settings to help stay hidden, so if you’ve been infected previously, there’s a chance the report will find something useful. But we’d like to see it updated with a more in-depth look at your system and application settings.
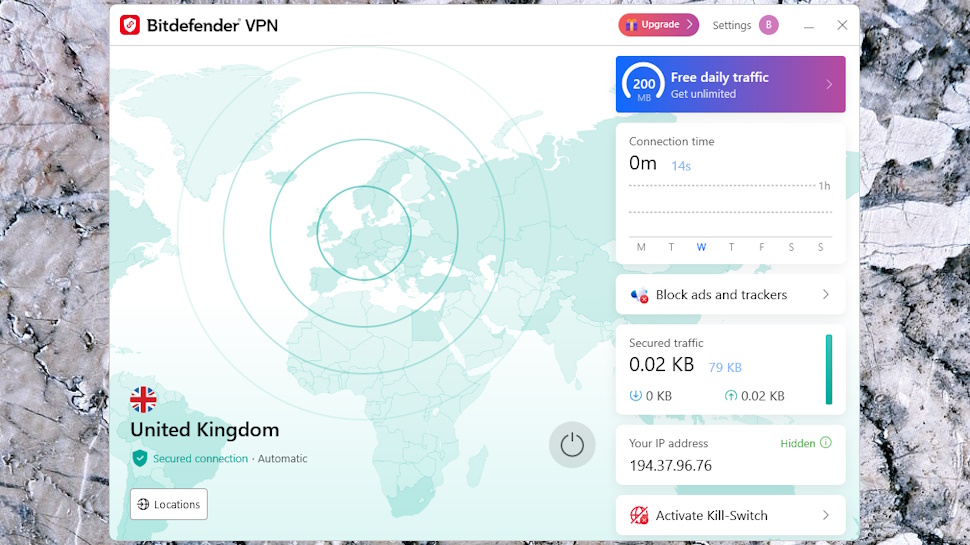
Bitdefender Antivirus Plus: VPN
Bitdefender Antivirus Plus includes the free version of Bitdefender VPN. The paid edition is an excellent service with quality apps using the Hotspot Shield network, but, unfortunately, the freebie is so restricted that many will find it unusable.
You only get 200MB of data a day, for instance. We opened desktop Outlook and a few other applications on a Windows laptop, and the background traffic alone used 70MB of data over the next hour. The free Bitdefender VPN is only suitable for light use.
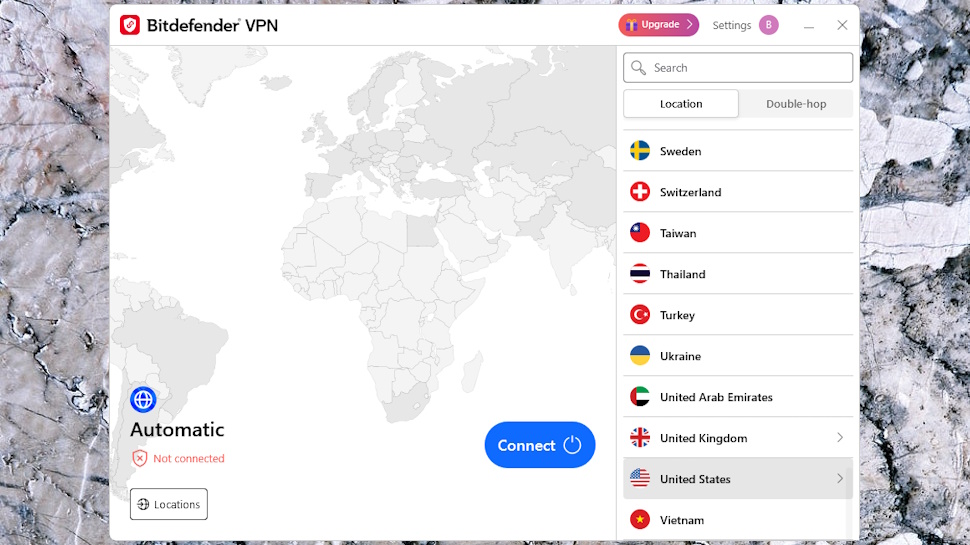
The other big issue is you can’t choose your location. Hit Connect and Bitdefender VPN automatically selects whatever it thinks is the best server for you (the closest or the fastest, most likely.). That means there’s little hope of unblocking anything, and, if the VPN chooses a location in a neighboring country to you, there’s nothing you can do about it.
Still, if you only need a VPN very occasionally, perhaps to securely access your email on public Wi-Fi, the free Bitdefender VPN just might be enough. And, if you can live with the data and location limits, there’s a lot to like here.
Bitdefender Antivirus Plus: VPN Features
Bitdefender’s Windows app takes up a lot of screen space, thanks to a large and mostly pointless map (you can’t pan or zoom, it doesn’t show Bitdefender’s location or even precisely highlight your own location when connected.) But it looks good, and provides a lot of information: your current IP address, the session length, the data you’ve used, and more.
Using the VPN is easy - just hit the blue Connect button - but connect times were relatively slow for us at around 6-8 seconds. Many WireGuard VPNs take only a couple of seconds, and ExpressVPN’s Lightway protocol often gets us connected in less than one second.
Speeds were very acceptable during testing at 60Mbps+ on a 70Mbps connection. That’s adequate for browsing, or a short period streaming if you turn the quality down (30 minutes of standard definition YouTube watching needs around 180MB, for instance.)
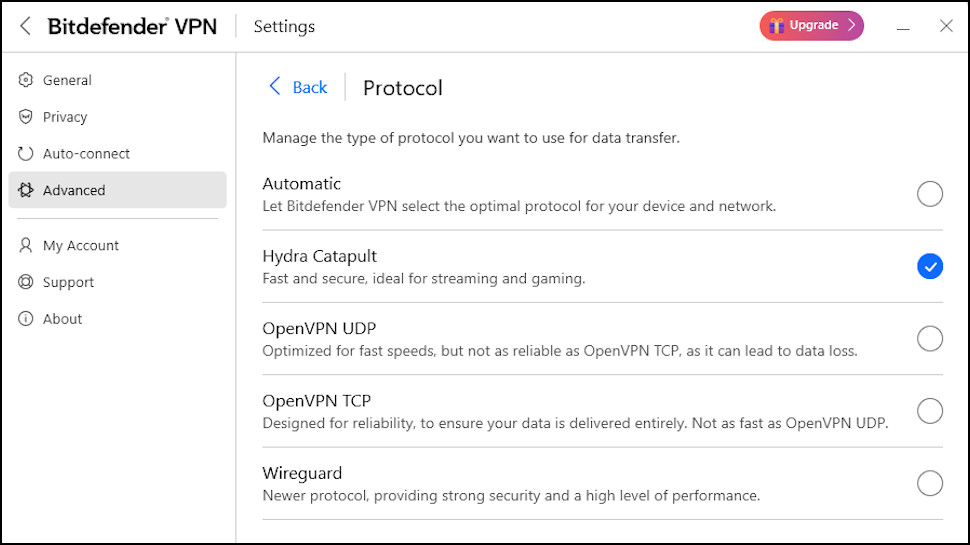
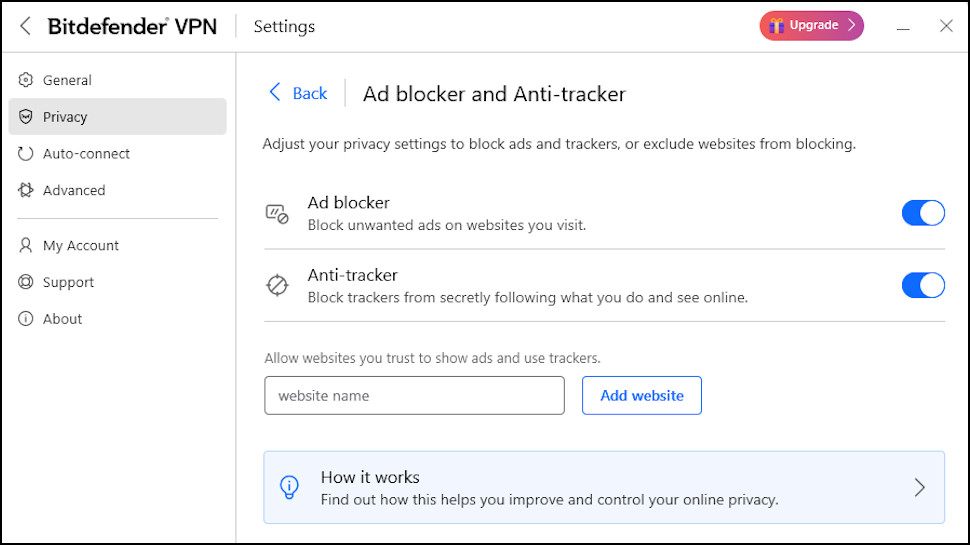
Bitdefender VPN’s highlight is its array of advanced features and configurations. Most VPN apps from antivirus providers are a little underpowered, but Bitdefender offers more functionality than many specialist VPN providers.
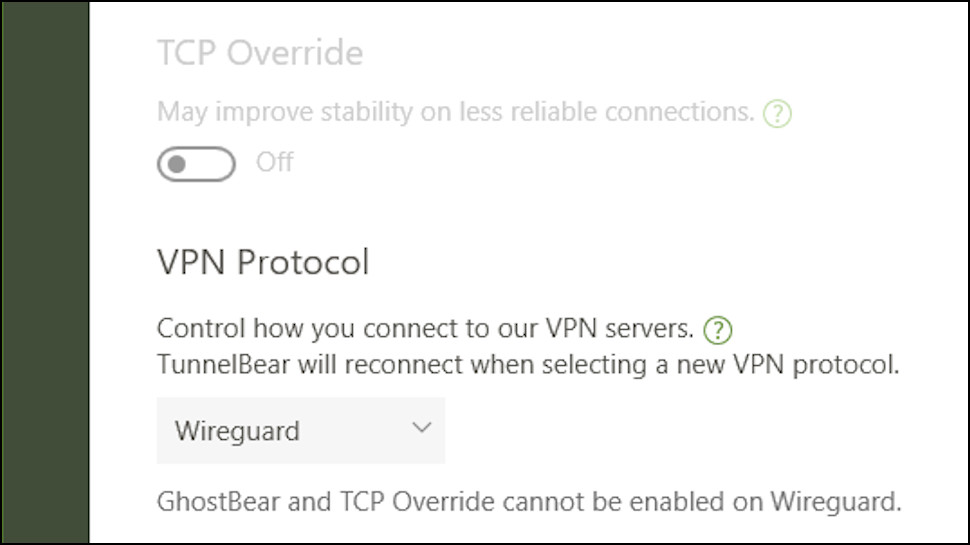
A strong choice of protocols includes WireGuard, OpenVPN and Hotspot Shield’s Hydra, for instance. Quality ad and tracker blocking enhances your privacy online, and we found the effective kill switch immediately blocks your internet access if the VPN drops.
Split tunneling support allows you to select apps which bypass the VPN and use the internet directly. That could help cut your VPN data usage and stretch that 200MB a day just a little further.
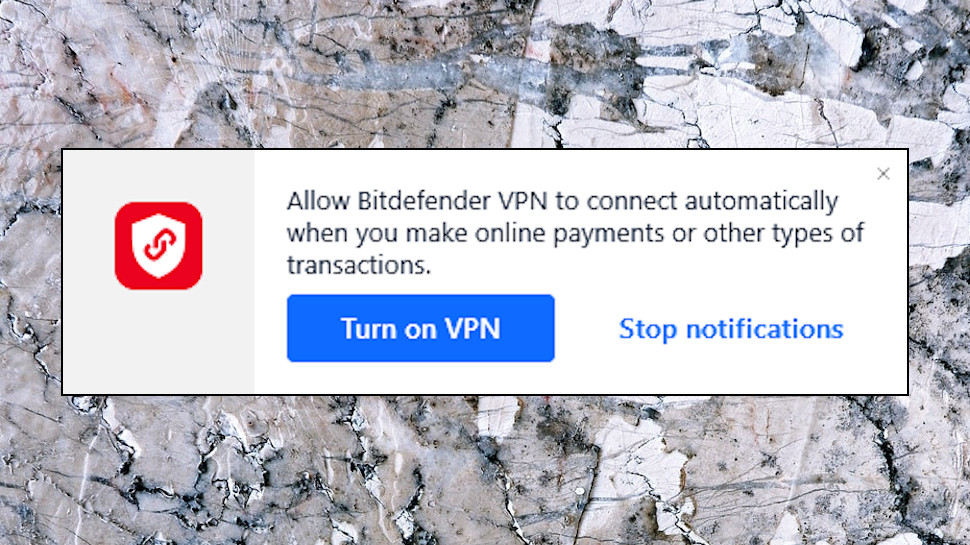
A very clever Auto-Connect option can automatically connect to the VPN when your device starts, if you connect to unsecured Wi-Fi, when you access specific domains (your business network, say), even if you visit a particular category of website: banking, online payments, health, and more.
There’s even an App Traffic Optimizer, which can improve speeds of up to three apps by giving them priority for your available bandwidth. That won’t help much with the free version - the more apps you use, the faster your data will disappear - but we have to applaud Bitdefender’s technical expertise.
Bitdefender Antivirus Plus: VPN alternatives
Bitdefender VPN might work for you if you only need the bare minimum of protection, perhaps to stay safe while you spend 15 minutes a day accessing the web on coffee shop Wi-Fi.
If you like Bitdefender but can’t live with the restrictions, upgrading to Bitdefender Premium Security adds the unlimited Bitdefender Premium VPN. It’s more expensive at $79.99 in year one, $159.99 on renewal, but that’s still fair value. NordVPN’s Basic plan costs $68 in year one, for instance, $112 on renewal, for the VPN alone.
Other antivirus vendors offer free VPNs with a little more. Avast One Essentials gives you a far more generous 5GB a week data allowance, for instance, although it also doesn’t allow you to choose a location.
You could also choose a provider from our best free VPN list. PrivadoVPN, for instance, allows you to choose from 12 locations, and has a far more flexible 10GB monthly data allowance. Well worth a look if you’re on a strict budget.
Bitdefender Antivirus Plus: Password Manager
Bitdefender Antivirus Plus includes a password manager on its feature list, but it’s only a three-month trial version. That still beats Avast, who dropped its own password manager a few years ago, but it can’t match Norton, who still includes a password manager with even its starter Antivirus Plus package.
We signed up for the trial anyway, an ultra-easy process which took just a couple of clicks. Bitdefender supports Password Manager on desktops via Chrome, Edge and Firefox extensions, and there are mobile apps for Android and iOS.
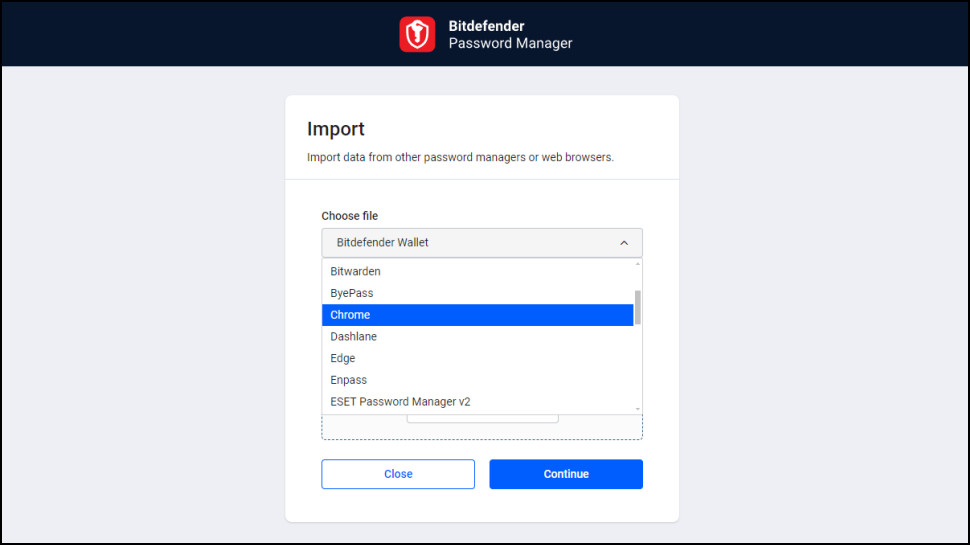
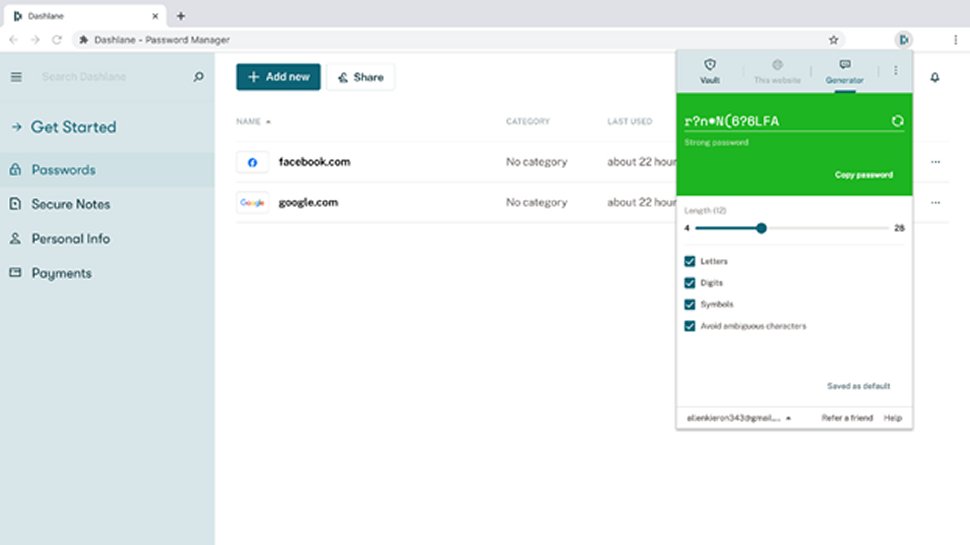
The tool supports importing existing passwords from many sources, good news if you’re looking for a quick start. There’s direct support for 1Password, Bitwarden, Chrome, Dashlane, Edge, Firefox, KeePass, LastPass, Roboform, Sticky Password and many more.
We tried importing data from Dashlane, and it mostly worked, with one issue. Dashlane supports multiple accounts for a website (same email address, different passwords); Bitdefender Password Manager doesn’t, so where Dashlane had multiple accounts, it imported one and ignored the others.
We found some issues with the tool in real-world use. When we complete a ‘new account’ web form with Dashlane, it recognises fields like ‘email’ and allows us to fill them with a click; Bitdefender does this with passwords, but we had to enter our email address manually.
Although Password Manager correctly captured simple ‘username and password’ screens, it sometimes failed with more complex forms. When one site asked for our name, email and password, for instance, Password Manager recorded the login as our name instead of our email.
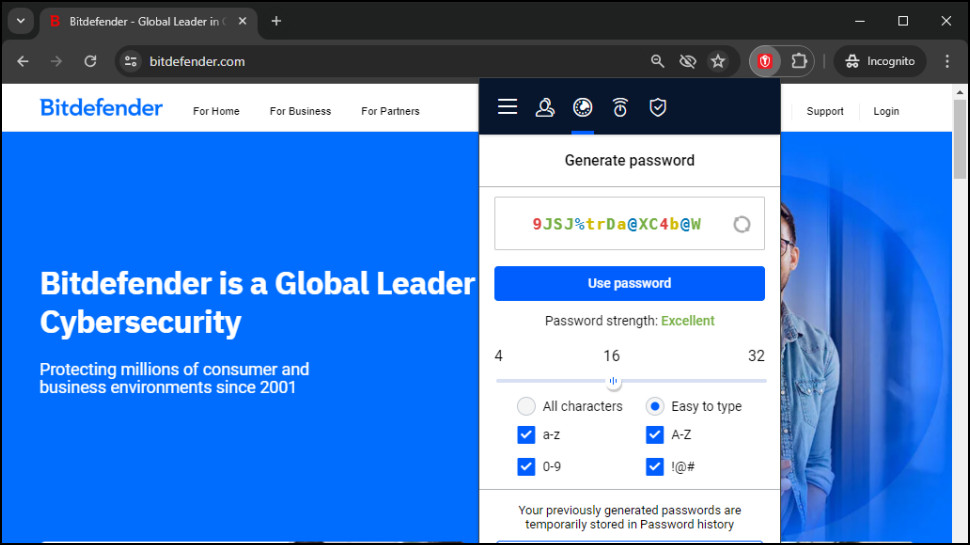
But there are plenty of plus points, too. It was easy to access our logins and copy usernames and passwords as required. A secure password generator creates strong passwords as you need them, with your choice of upper case, lower case, numbers and symbols (and a neat ‘easy to type’ option to avoid the harder-to-find symbols.) The Security Report highlights weak or reused passwords, and can even run a leaked password check (via haveibeenpwned.com) to see if your account appears in any data breaches.
Bitdefender Password Manager is a useful tool, especially if you get it for free as a part of Bitdefender Ultimate Security or Bitdefender Premium Security. If you need to buy Password Manager separately, it’s cheap at $19.99 for year one, $29.99 on renewal (that’s half the price of Dashlane.) But if you’re looking for a powerhouse password manager with every possible feature, check our Best Password Manager guide for better ideas.
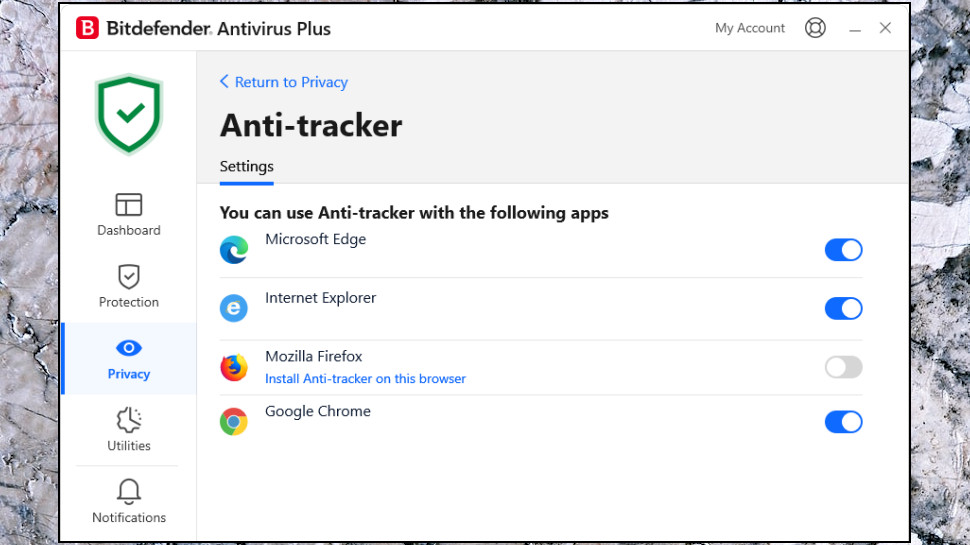
Bitdefender Antivirus Plus: Anti-tracker
Bitdefender’s Anti-tracker feature is a technology that prevents intrusive trackers from collecting data on your online activities.
Anti-tracker is available as a very easy-to-use browser extension for Chrome, Edge and Firefox.
We installed Anti-tracker on Chrome and it began blocking threats immediately, with nothing else to configure. You can leave the service to do its work, or, if you’re curious, click the extension icon for a report on whatever it’s blocked on the current page.
Our tests showed Anti-tracker blocked an excellent 93% of sample trackers. But we found that it also blocked trackers that are essential to website functionality. View the radar maps on weather.com, for instance, and although you’ll see radar images of incoming weather, the site doesn’t display cities, roads or any of the underlying map. Reading user reviews, we found many similar complaints of Anti-tracker breaking websites.
You can address this, in theory, by telling Anti-tracker not to block trackers on sites where you notice issues. But if, like weather.com, the only issue is a site not displaying some usual content, you may never realize there’s a problem. And the idea of having to exclude sites on Anti-tracker every single time something doesn’t work as you’d expect just feels too much time-consuming trouble than it’s worth. But if you disagree, give the extensions a try: they’re all free, no need to buy Bitdefender products or even create an account.
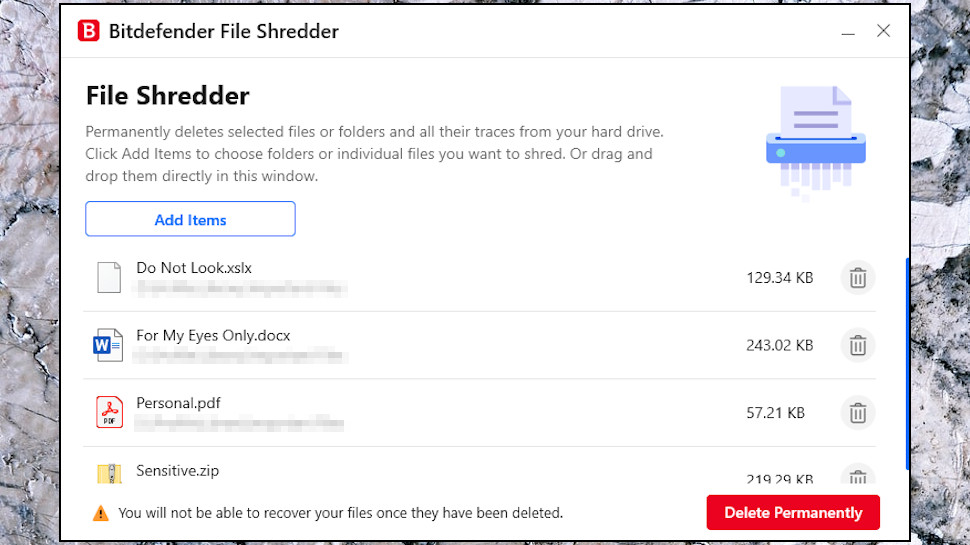
Bitdefender Antivirus Plus: File Shredder
Bitdefender’s File Shredder is a simple tool which securely deletes files by overwriting them multiple times. It’s an easy way to get rid of sensitive documents, and ensures that even if someone else has full access to your device (you’ve sold it, maybe it’s been stolen), they won’t be able to undelete or recover that dara.
The easiest way to make this happen is to choose the files in Explorer, then right-click and select Bitdefender > File Shredder. Your files appear in the File Shredder console, and you can wipe them all forever with a click.
There are no configuration options, which might be an issue for the demanding expert users. For example, specialist secure deletion tools often allow you to choose a wiping algorithm, perhaps to overwrite data more often for extra security.
File Shredder delivers all the functionality most users will ever need, though. It doesn’t add a lot of value to the suite because there are more powerful file wiping tools available for free, but File Shredder’s ease of use is a plus, and overall we’re glad it’s included in the package.
Bitdefender Antivirus Plus: Final verdict
Bitdefender Antivirus Plus consistently delivers great PC malware protection results from the top independent testing labs and in our own checks. But where it really scores is in Bitdefender’s array of additional security layers, including effective anti-phishing to block dangerous websites, and multi-layered ransomware protection that can recover damaged files in seconds. It’s our top Windows antivirus, and a must-try for anyone with a PC to protect.
Read more Bitdefender reviews: