Proton has established itself quite successfully in the world of security products. You may have heard of its offerings in the encrypted email and VPN industries. Well, it also has a superb answer to the best password managers in the form of Proton Pass.
This handy password manager promises end-to-end encryption for all your passwords, ensuring your sensitive data remains secure even from Proton itself. It supports 2FA, encrypted notes, and even email alias generation - all packed into Proton's signature user-friendly interface. And just like all of Proton's offerings, its open-source and regularly audited by security experts.
But does Proton Pass live up to its reputation for privacy and ease of use? With competition from established players, can a relatively new password manager carve out a space for itself? Let's take a look.
Proton Pass: Plans and pricing
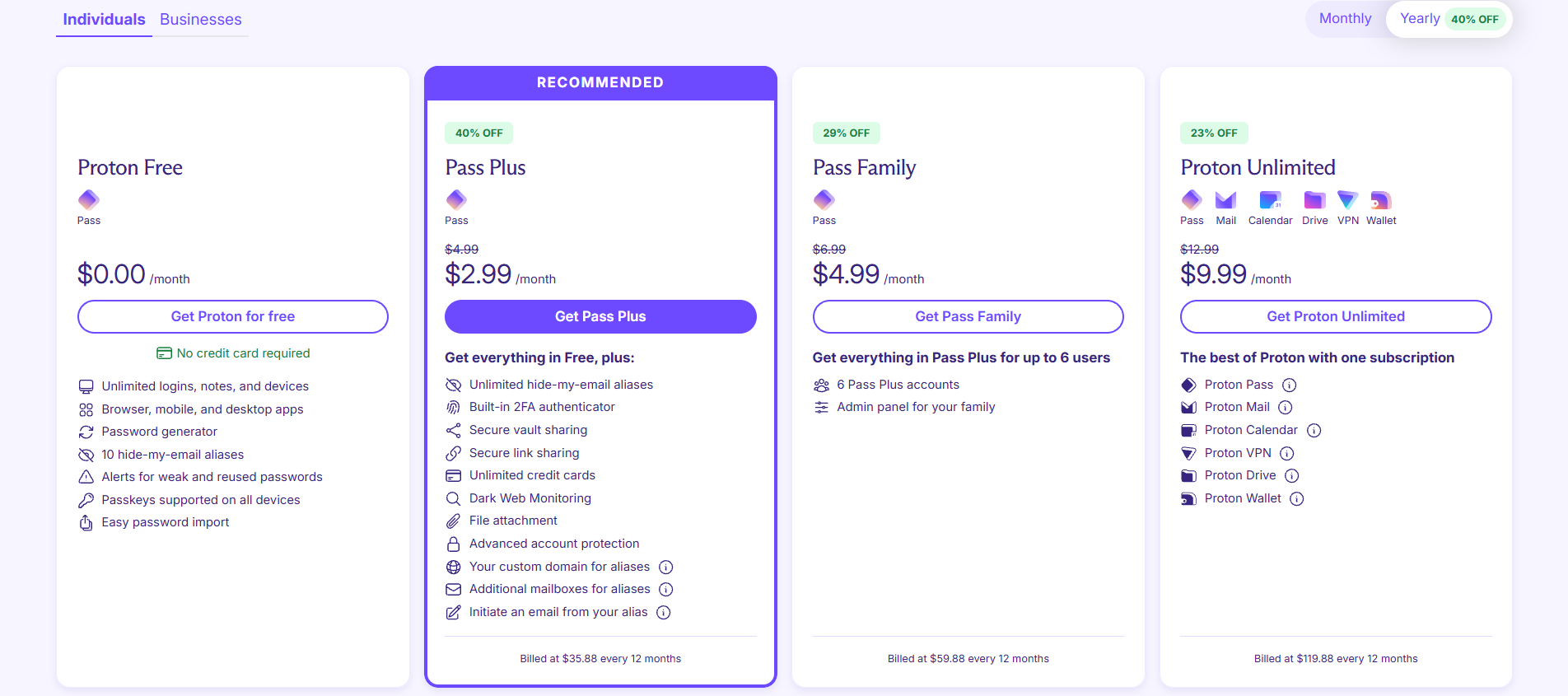
Proton Pass offers a range of pricing options to suit different needs. The Free plan provides a solid foundation with unlimited passwords, support for passkeys, and two vaults, all protected by end-to-end encryption. For users seeking enhanced privacy and convenience, the Plus plan, priced at $2.99/month with an annual subscription, unlocks access to the Proton Sentinel service, unlimited hide-my-email aliases and premium support.
The Proton Pass Family plan is $4.99 per month, when paid for a year, and it allows up to six people to experience everything the Proton Pass Plus offers.
Those who want a comprehensive suite of privacy tools can opt for Proton Unlimited at $9.99/month with an annual subscription, which includes all Proton services like Mail, VPN, Drive, Calendar, and Pass.
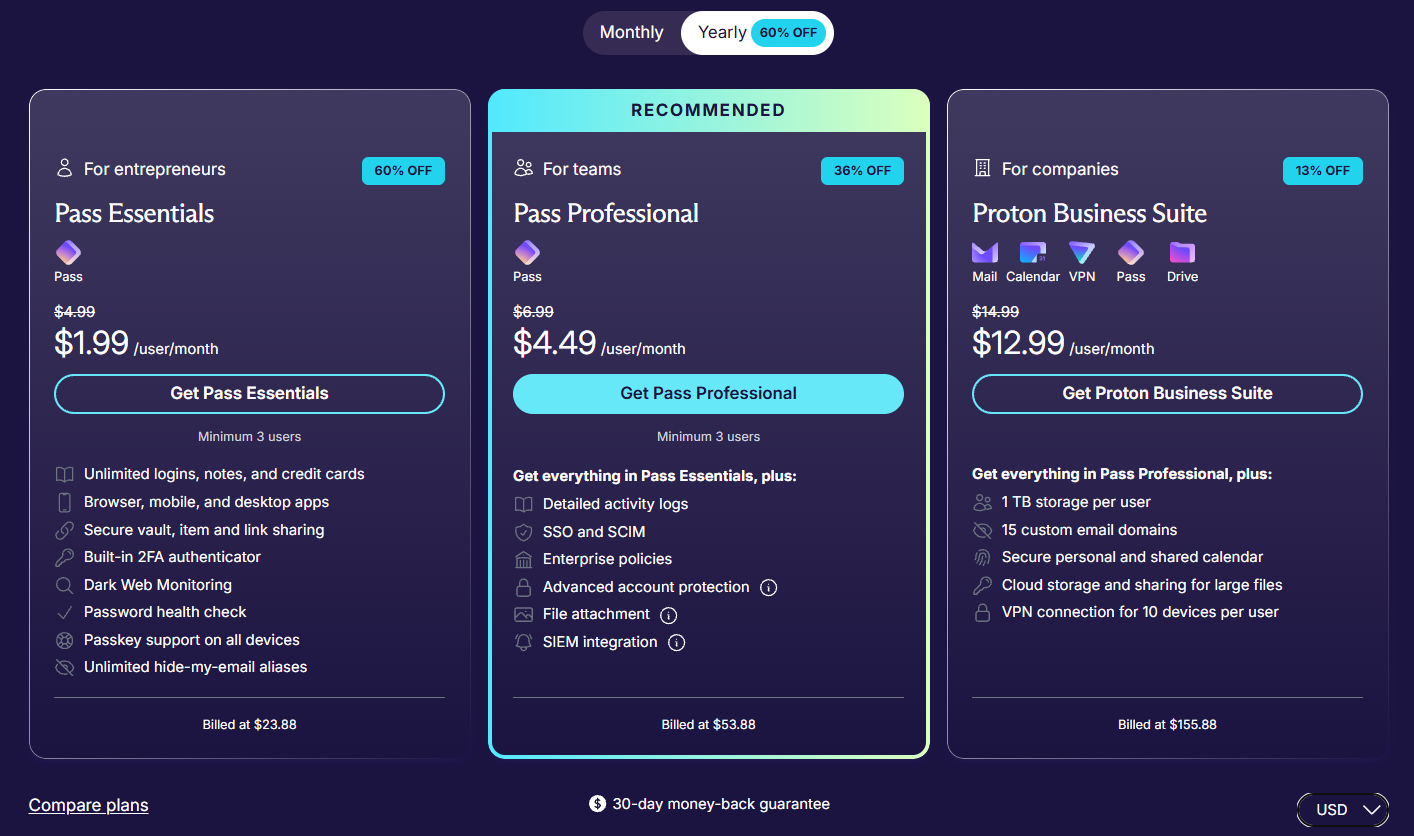
The Business plans start with Pass Essential that costs $1.99/user/month when paid for a year (yearly total $23.88/user). It includes all the essential password management features such as the ability to store unlimited passwords, passkeys, notes, and credit card details, a built-in 2FA authenticator, and unlimited email aliases.
For larger organizations that need support for single sign-on (SSO), and detailed activity logs, there’s Pass Professional that costs $4.49/user/month with an annual subscription (yearly total $53.88/user). You’ll have to pay for a minimum of three seats for both Pass Essential and Pass Professional plans.
Proton Pass: Setup
Here’s an overview of how to set up Proton Pass.
First and foremost, it's important to have a Proton account. If you still need to create one, visit the Proton website and sign up for an account. Once you've registered and verified your credentials, you'll need to enable two-factor authentication (2FA), which is where Proton Pass comes into play. Two-factor authentication adds a level of security by requiring your password and a unique code that you can access only at the time of login.
To set up 2FA and Proton Pass, log in to your Proton account and navigate to the security settings page. Here, you will find the option to enable two-factor authentication. Click on it, and you'll be prompted to download a two-factor authentication app if you haven't already. Proton recommends using an authenticator app like Google Authenticator, Authy, or FreeOTP, which you can download from your mobile app store.
After installing the authenticator app on your smartphone or tablet, the next step is to link it to your Proton account. Within the Proton security settings, a QR code will appear on the screen. Open your authenticator app and use its 'Scan QR code' feature to scan this code. This will automatically add your Proton account to the app and generate timed, one-time passcodes.
The Proton security settings page will also provide you with a recovery code. Writing this down or printing it and keeping it somewhere safe is crucial. This code is a lifeline for instances where you might lose access to your second-factor device. With your authenticator app now synced, your Proton Pass is effectively set up. When you log in to your Proton account, you will enter your password and the unique code displayed in your authenticator app.

Proton Pass: Interface and performance
The Proton Pass interface is a masterclass in minimalist design, reflecting Proton's philosophy of providing simple yet powerful security solutions. Activating two-factor authentication (2FA) for your Proton account reveals a clean and intuitive dashboard that seamlessly blends user-friendliness with robust security.
Navigating to 2FA settings is effortless, with clear instructions and visuals guiding you through the setup process. The prominent display of the QR code for your authentication app ensures quick and easy account linking. Proton Pass excels in its handling of the recovery code, prominently showcasing it during setup and stressing its importance for account recovery. This thoughtful design prioritizes user understanding and preparedness.
Once set up, using Proton Pass becomes second nature. The login process is streamlined, requiring your password and 2FA code in a clear, two-step sequence. Input fields are unambiguously labeled and positioned for a frictionless experience. This commitment to simplicity extends throughout the interface, minimizing distractions and cognitive load to ensure a smooth and efficient authentication process.
The aesthetic minimalism of Proton Pass isn't just about visual appeal; it's a deliberate strategy to enhance usability and encourage secure practices. By prioritizing clarity and ease of use, Proton Pass empowers users to take control of their online security without unnecessary complexity.
Proton Pass: Security
Proton Pass takes a multi-layered approach to security, aiming to protect your passwords and sensitive data with the strongest possible safeguards:
End-to-End Encryption: This is the cornerstone of Proton Pass's security. All your data, including passwords, usernames, notes, and even website addresses and metadata, is encrypted on your device before it's sent to Proton's servers. This means that no one, not even Proton themselves, can access your information in its unencrypted form.
Zero-Knowledge Architecture: Proton Pass operates on a zero-knowledge principle. This means that your encryption keys are generated and stored only on your device. Proton has no access to these keys, further ensuring that they cannot decrypt your data.
Strong Encryption Algorithms: Proton Pass uses both asymmetric and symmetric encryption algorithms to secure your data, including AES256 and OpenPGP. These are industry-standard algorithms known for their resilience against brute-force attacks and other security threats. Proton Pass also encrypts stored passkeys using Curve25519.
Open Source: Much of Proton Pass's code is open source, allowing security researchers and the community to audit it for vulnerabilities. This transparency helps ensure the integrity and security of the software.
Two-Factor Authentication (2FA): Proton Pass supports 2FA, adding an extra layer of security to your account. This requires a unique code from your authentication app in addition to your password when logging in, making it much harder for unauthorized access. As an additional bonus, Proton Pass also offers an in-app authenticator and will let you know when 2FA can be enabled on any of your stored accounts.
Password Generator: Proton Pass includes a strong password generator that can create complex, unique passwords for each of your accounts, reducing the risk of password reuse and vulnerability to breaches.
Breach & Dark Web Monitoring: Proton Pass can monitor your accounts for data breaches and alert you if your information is compromised. This allows you to take immediate action to protect your accounts.
Proton Sentinel: For users in need of extra protection, Proton Pass also offers protection from it's Proton Sentinel high-security program which includes additional security protections, enhanced visibility into security logs, 24/7 suspicious login monitoring using both AI and human detections, and automatic security specialist referral for all account security support requests.
Hide-my-email Alias: Proton Pass also makes your email more secure by offering a fully integrated email masking tool that allows you to customize your masked domain and alias, and allows you to forward mail that is sent to your masked email to multiple inboxes.
Secure sharing: Outside of secure sharing with other Proton users, you can securely share vaults, links, and files with non-Proton users.
Secure payments: Proton Pass will let you securely store an unlimited amount of credit cards.
In summary, Proton Pass employs a comprehensive suite of security measures to safeguard your sensitive information. Its focus on end-to-end encryption, zero-knowledge architecture, and open-source practices makes it a highly secure choice for password management.
Proton Pass Business: Team and Admin Features
Proton Pass Business offers adequate team management and administrative capabilities.
As is the norm for such offerings, Proton Pass Business offers a web-based centralized admin console for managing users, controlling permissions, and monitoring password health, and user activity.
Your users can use the platform to create organization-wide, or department, and team-specific vaults to share credentials, and other secure data. Users can share the vault with other users in the same team or department, with granular access permissions.
By default, the invited users can only view the items in a vault, but they can also be given Edit permissions to create, delete, and export items in the vault, or Manage permissions to grant, and revoke access to a vault to other members.
As an admin, you can prevent users from sharing vaults with others who aren’t part of your organization. In addition to vaults, you can also prevent your users from sharing individual items, and stop them from exporting their data as well.
If you do allow sharing of individual items, your users can share passwords, and other sensitive information, such as secured notes, with their colleagues.
They can also share these with anyone, even if they don’t use Proton Pass, with Secure Links. The feature helps create unique, expirable links to your login credentials, secure notes, and other items. You can set the expiration date from anywhere between one hour up to 30 days, and even restrict the number of times the recipient can access the link (from one to as many).
That said, you can’t control which devices can access company vaults. Neither can you restrict access by IP address.
You can use Proton Pass Business to define password policies. The platform gives you the ability to enforce password complexity requirements, including the ability to customize minimum and maximum password length, and whether they should include numbers, special characters, and uppercase characters.
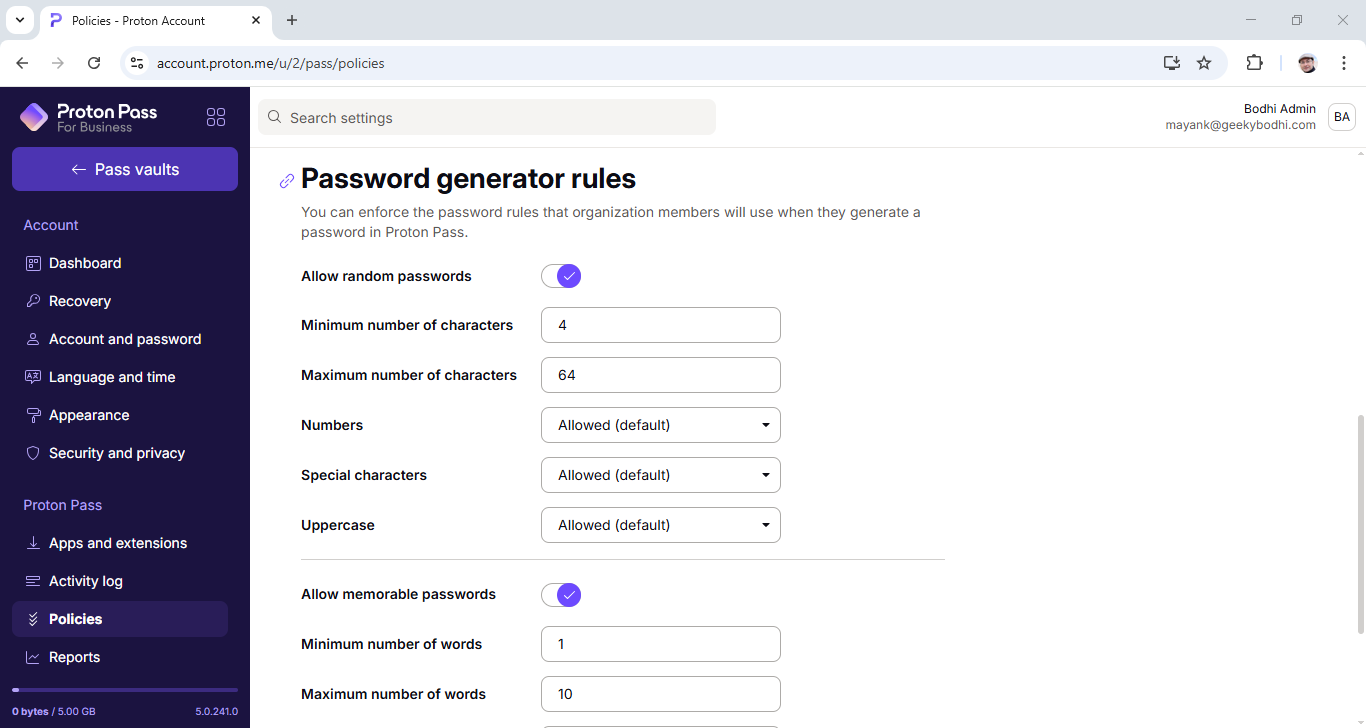
One interesting option is the ability to ask the platform to help your users generate memorable passwords. That said, unlike some of its peers, the platform doesn’t allow admins to enforce a password rotation policy on its users.
Another strong security feature is the ability to require all your users to use 2FA. If you don’t want to force this upon them, you do have the option to gently remind them (via email) to enable 2FA on their own.
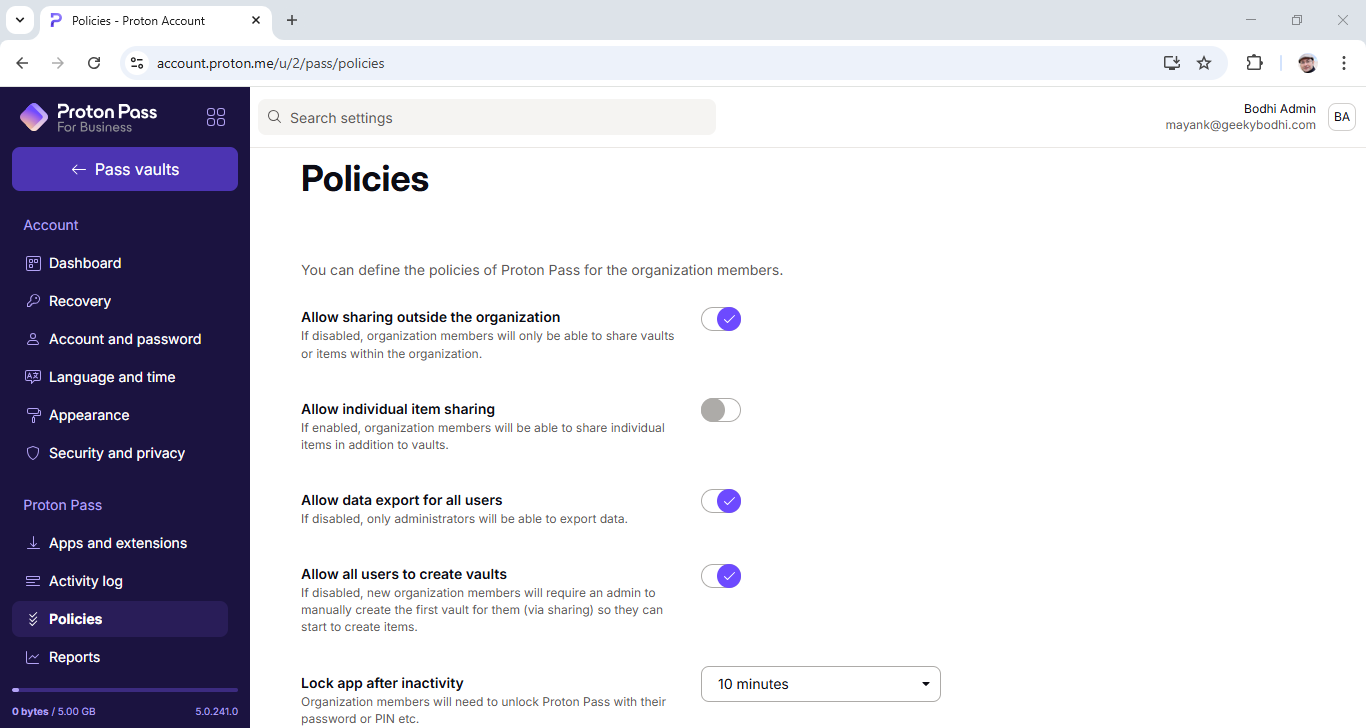
The platform also lets admins forcefully logout users after the expiry of a configurable idle period, which can range from one minute to one hour. Here too we miss a failed login attempt feature that you get with some of its peers, which locks accounts after detecting suspicious activity, like a number of failed logins.
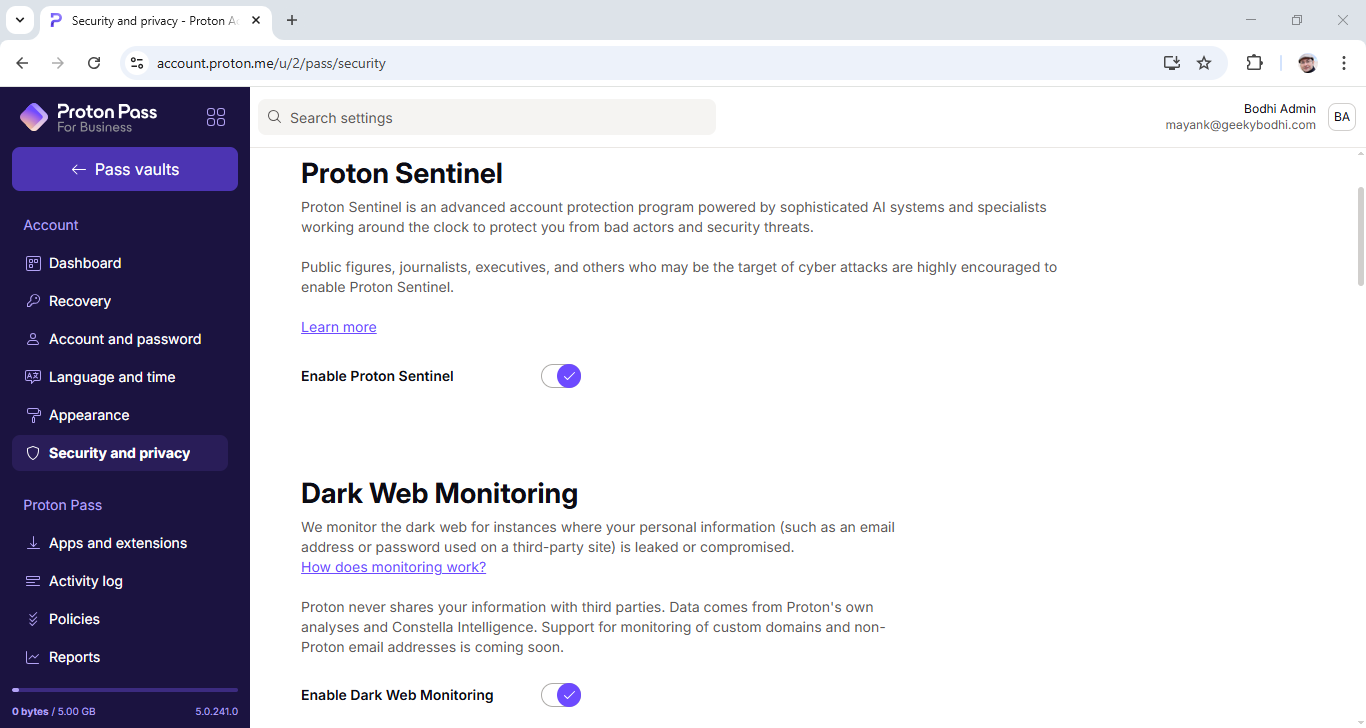
Talking of suspicious activity, Proton Pass Business gives users access to a Pass Monitor feature that monitors the dark web for leaked passwords, and more. Business users are also enrolled in the Proton Sentinel program, which helps detect and stop unauthorized attempts to break into your account, even if the attackers have the correct password.
Finally, the platform offers detailed activity logs that help give visibility over all kinds of user activity, such as any changes made to passwords and vaults. The platform is pretty comprehensive in its logging, and tracks about two dozen events, for everything from invitations, and vaults, to individual items, and secure links.
Proton Pass Business: Integrations and Compatibility
Proton Pass works across platforms, and offers native apps for all the popular desktop and mobile operating systems, namely Windows, macOS, Linux, Android, and iOS. It also offers extensions for the best web browsers including Chrome, Brave, Firefox, Safari, and Edge.
Proton Pass can import passwords from any of these browsers, as well as from the best password managers including 1Password, Bitwarden, Dashlane, Keeper, NordPass, RoboForm, and others.
If you are a Pass Professional user, you also get support for SSO and SCIM integration. Proton Pass Business plugs into all the mainstream identity providers (IdPs) like Microsoft Entra ID, Okta, and Google Workspace to streamline user lifecycle management.
Finally, as we have mentioned earlier, Proton Pass is also deeply integrated into the Proton ecosystem of services, including Proton Mail and Calendar, Proton Drive, Proton VPN, and Proton Wallet. As an admin you can control which of these services can users in your organization access.
Proton Pass Business: Ease of Use and Deployment
The admin panel of Proton Pass Business is clean, and fairly intuitive.
The first order of business is user provisioning, and the platform offers adequate options to help admins add (and later remove) team members.
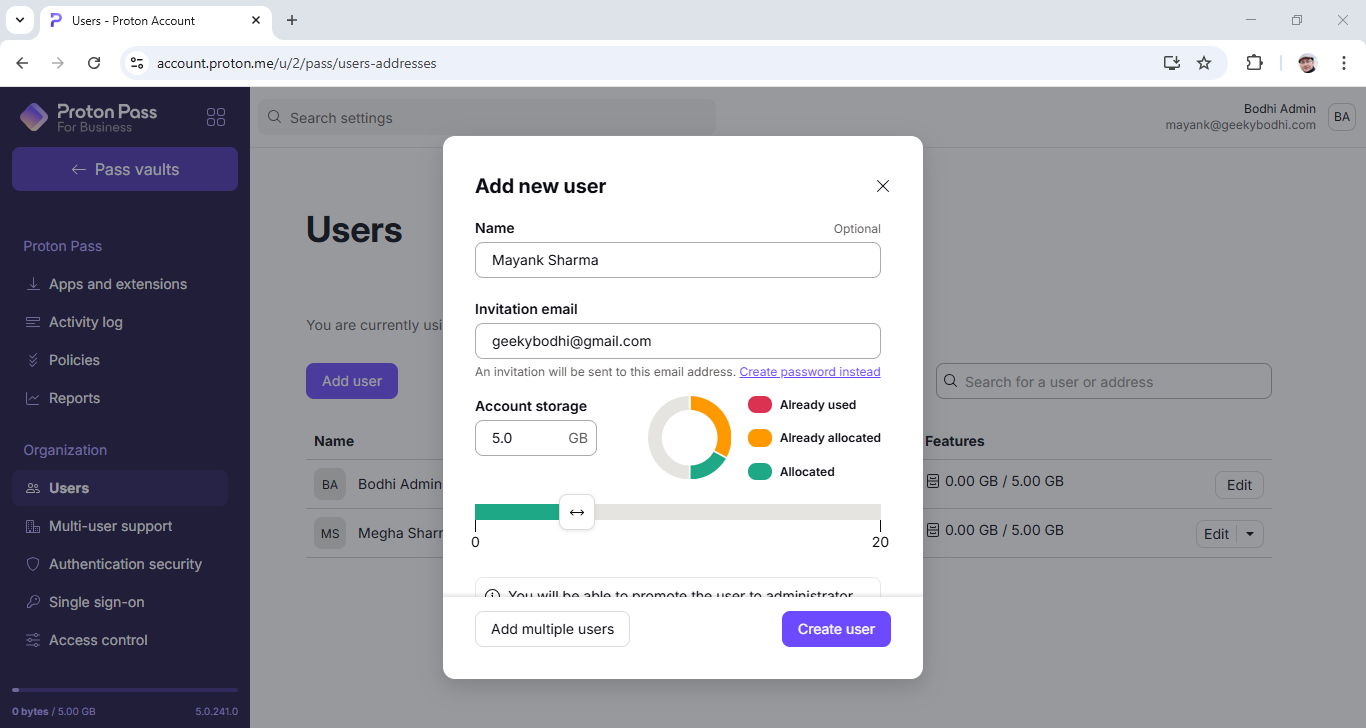
Admins can invite members by sending them an email. You can also directly create a password for them, instead of sending them an invite, and then share the password with them using other secure means. The platform also offers bulk user import through CSV files.
In the same vein, the process of enabling SSO for the supported IdPs is also fairly intuitive, and is well documented. Once added, you can give admin privileges to other users, although only the primary admin can edit the plan of the organization.
Admins can track the activity of their users through the Reports section. It offers a Pass Monitor report that tells you the number of reused, weak passwords, if the passwords were found in any breach, and other details, for every user. Then there’s the Usage report that tells you the total number of items a user has access to, the number of vaults they own, and have access to, and other details, again for every user.
Finally, there’s the Activity Logs section that logs all user events along with their time, the user account that it happened on, the type of event, and the IP address the activity originated from.
You can filter the logs by email or IP address, event type, and date range. You can also click on a time or event entry to filter by that timestamp or event type. Both the reports, and the activity logs can also be exported as a CSV file.
Proton Pass: Customer support
Like any other company, Proton has a wealth of online guides to help you set things up and carry out basic troubleshooting and other issues. There are also helpful tabs on the latest Proton Pass updates and guides to enhancing personal privacy.
Getting in touch is easier than with some bigger companies, as there’s a clear form that’s easy to find, though responses will be by email rather than live chat. As more Internet users begin to question and value their privacy, turning to Proton and other security-focused products, we can only hope that the company invests in multi-channel support, be it live chat, social media support, or a phone number. Fortunately, it looks like all customers, free or paid, are treated equally.
Proton Pass: The competition
Proton Pass is not short of competition, and frankly the password management market is fairly saturated. However, Proton's open-source basis and wealth of security tools and features make it a very strong contender.
It's rivals include the likes of NordPass, which offers more competitive pricing with a similar feature set. For business oriented customers, 1Password is slightly more expensive but offers 24/7 support, however a business looking for a dedicated suite of secure business products may benefit from signing up to the full Proton Business Suite to access Mail, Calendar, VPN, Pass, and Drive for just a few extra dollars per user per month.
Proton Pass: Final verdict
Proton Pass simplifies strong security with its intuitive two-factor authentication (2FA) interface. Setting up 2FA is a breeze, thanks to clear instructions, a streamlined recovery process, and an uncluttered dashboard. While Proton Pass makes robust cybersecurity accessible to everyone, deciding whether to use it depends on your specific needs.
If you regularly handle sensitive information, Proton Pass provides a significant security boost, protecting your account from potential breaches. However, if you rarely deal with sensitive data or find 2FA workflows disruptive, alternative security measures might be sufficient.
Ultimately, choosing Proton Pass is about your commitment to online security. It's an extra step in your authentication process, but one that significantly strengthens your defenses and protects your digital identity.
We've also featured the best business password managers.
What to look for in a password manager
Choosing a password manager is a crucial step towards safeguarding your digital life. With so many options available, it's essential to prioritize features that guarantee both security and a seamless user experience. Here's a breakdown of key factors to consider:
Security is Paramount:
Robust Encryption: Look for a password manager that employs industry-leading encryption standards like AES-256. This ensures your sensitive data remains unreadable even if a breach occurs.
Zero-Knowledge Architecture: Prioritize providers who utilize a zero-knowledge model, meaning they cannot access your encrypted data or master password. This puts you in complete control of your information.
Two-Factor Authentication (2FA): Enable 2FA for an added layer of security. This requires a unique code from your authentication app in addition to your master password, making it significantly harder for unauthorized access.
Open-Source Options: Consider open-source password managers. Their transparent code allows for community scrutiny and independent security audits, ensuring higher trustworthiness.
Usability Matters:
Intuitive Interface: A user-friendly interface is essential for effortless password management. Look for features like easy navigation, clear organization, and a straightforward password generation process.
Cross-Platform Compatibility: Ensure the password manager seamlessly integrates across your devices (desktops, laptops, smartphones, tablets) and various operating systems (Windows, macOS, iOS, Android).
Auto-fill and Password Generation: These features streamline your online experience. Auto-fill automatically populates login credentials, while the password generator creates strong, unique passwords for each account.
Beyond the Basics:
Password Health Check: A good password manager should assess your existing passwords for strength and identify any weak or reused ones, helping you improve your overall security posture.
Breach Monitoring: Some password managers offer breach monitoring, alerting you if your credentials are compromised in a data breach. This allows for swift action to secure your accounts.
Secure Sharing: If you need to share passwords with family or colleagues, look for secure sharing features that maintain encryption and control over access.
Provider Reputation and Support:
Reliable Customer Service: Choose a provider with responsive customer support to assist you with any issues or questions.
Regular Updates: Frequent updates demonstrate the provider's commitment to security and addressing potential vulnerabilities.
By thoroughly evaluating these factors, you can select a password manager that not only protects your digital identity but also simplifies your online experience. Remember, a good password manager is an investment in your online security and peace of mind.






