Fabian Wosar makes a living ruining ransomware gangs’ days, and he has the hate-mail to prove it.
“At one point, I managed to annoy a ransomware author so much that they literally renamed their ransomware in my name,” he says. “So they renamed their ransomware to ‘fabiansomware’, which is kind of really bizarre.”
Wosar is the head of research at IT security company Emsisoft, whose free ransomware decryption tools have been downloaded over a million times (1,144,351, to be exact, not including downloads from mirror sites). With the average ransomware writer demanding $522 (about £400, AU$750) to restore victims’ files, that’s a potential $597,351,222 (about £455,000,000, AU$833,000,000) kept out of the pockets of ransomware authors. Not bad for a 40-person company without an office.
“Emsisoft started out as a very, very small company with only two employees,” says Wosar. “When you try to get into the antivirus and antimalware field and you only have two people, there’s no way you can compete based on manpower with the big houses like Symantec and Kaspersky or Bitdefender, which all have thousands of employees.
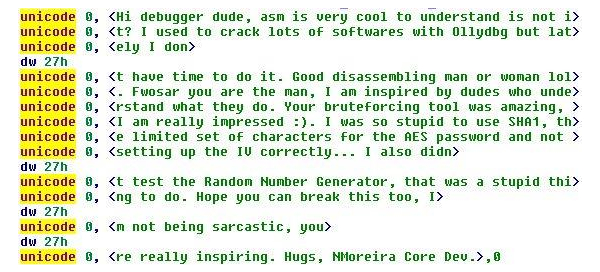
Not all the comments Wosar receives are insults; some ransomware authors are impressed
“It was very evident from the very beginning that we just have to be more agile, that we need to make sure that all our internal processes have a lot less overhead and we also had to be a lot smarter about how we put our limited resources to good use. And this business mindset that was originally born as kind of a necessity soon became the core philosophy behind all our products.
Emsisoft has grown steadily over the last 15 years, with no outside investment. It’s still a lot smaller than many of its rivals, but that hasn’t stopped it competing with the security software giants.
“We started out very much as a very home user focused company,” Wosar says, “but we started moving into the business market in recent years, with growing success and we came to realise that home users and enterprises often have vastly different requirements and needs. Most traditional companies solve that by just throwing more resources at it, and often splitting the product line, having different products for different clienteles, but that’s something that we simply can’t do.
“So our philosophy of keeping things lean we now focus on making all these advanced enterprise-level protection features not only available to home users, but also to make them approachable and useful to them so they can actually understand them and know what is happening, and putting the user into power by making them a lot more accessible, which will become a lot more eminent with a couple of upcoming products that we are going to release in 2019 that I can’t tell much about. But that’s out focus now, just giving the power to the man.”
A brief history of ransomware
Wosar’s interest in security began when he was just 11. “I got infected by a virus called Tequila in the good old DOS days, and I just got kind of drawn in,” he says.
He first became interested in ransomware in 2012, when BleepingComputer founder Lawrence Abrams asked if he could help some forum users who’d fallen victim to the ACCDFISA (Anti Cyber Crime Department of Federal Internet Security Agency) virus – one of the first examples of file-encrypting ransomware.
“Ransomware first became big in the form of screen lockers,” Wosar explains. “Essentially you’re browsing the internet and suddenly a screen pops up locking your entire screen, telling you the FBI or GCHQ just saw you doing something naughty. Now you have to go to your local store and pick up a Paysafecard and type in the code to unlock your system. Because obviously the state would take Paysafecard, right?”
That is always kind of interesting, when people get so angry that they want to insult me so badly that they actually end up making their ransomware less secure in the process
Fabian Wosar, Emsisoft
It soon became common knowledge that screen lockers were relatively easy to remove (just restart the computer in Safe Mode and remove the infection), so the people behind them turned to file encryption instead. This is a much bigger issue, and one that Wosar has dedicated years to tackling – much to the annoyance of the criminals.
Wosar receives regular insults, and often finds them within the ransomware itself, which can have unintended consequences.
“There’s a certain kind of encryption called a block cipher that operates on blocks of data,” Wosar says. “When you think about it, if you don’t change your encryption from block to block, then even if you only have an encrypted file, you could at least tell which parts of the file contain identical data because the encrypted blocks will stay the same as they were before. So if you have large parts that only contain zero bytes, for example, you could still see those parts.”
Wosar shares an example that’s well-known in the security community: an image of Tux the penguin, which has been encrypted using a simple block cipher, but is still clearly legible. To get around that problem, you need a block mode.
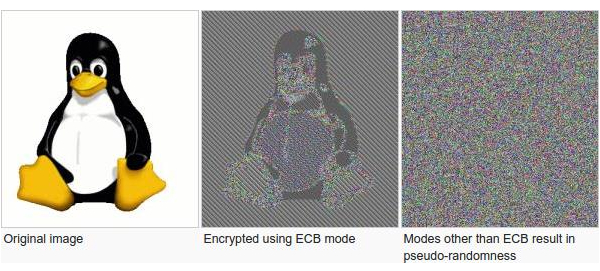
When an image is encrypted with a simple block cipher, parts can still be legible
“You can think of block mode as an extra step that you do to make the same block inside a file look different each time you encrypt it,” says Wosar, “and in order to do that, you start out with something that’s called an initialisation vector, or an IV. For this ransomware, they used an IV that contained data from memory that was just random. They didn’t put any specific data into the IV – they just took something random from memory, and whatever was in that memory before, that became the IV. Now when they added the insults, they actually put the insult into the IV. That means the IV was always the same after that, which reduced the security of their ransomware.
“So that is always kind of interesting, when people get so angry that they want to insult me so badly that they actually end up making their ransomware less secure in the process. So that’s kind of funny.”
Threats to home users
Ransomware writers are starting to learn that targeting home users isn’t particularly lucrative – partly because many don’t have the money to pay, and partly because they simply don’t care about the data that’s been encrypted.
“Most of the focus nowadays is on your mobile phone,” says Wosar, “and if you have a mobile phone, chances are it’s getting backed up to the cloud as well – to Google Photos or iCloud. If all your pictures on your system are encrypted, you can just download, so that’s not a big issue.”
Faced with home users who can’t or won’t pay, ransomware writers have begun to branch out. “If ransomware often finds itself on a system that is particularly powerful, or that has a very good graphics card for example, they often opt into not encrypting the files, but dropping something that is called a cryptominer onto the system,” Wosar says. “A cryptominer will then start mining cryptocurrency in the background, and trying to download that.
“Another trend that’s often seem with ransomware or malware in general is the introduction of cryptojackers, which are essentially little trojans or malware that looks on your system for cryptocurrency wallets and steal it. Financial malware is also still an issue for home users, trying to steal your banking credentials for example, or your PayPal credentials, in order for someone to then just access your bank account and steal all your money.
If ransomware often finds itself on a system that is particularly powerful, or that has a very good graphics card for example, they often opt into not encrypting the files
Fabian Wosar, Emsisoft
In addition to ransomware, Wosar says home users should also be aware of bots, which hijack your system and make it part of a remote-operated network called a botnet.
“You can think of that as a collective of systems that are under the control of a single entity, which is usually called the bot herder, and they can make your system do whatever they want, pretty much. In a lot of cases, though, these kinds of botnets are being used to distribute spam campaigns like send millions of spam emails.
“They can be used to launch DDOS attacks, so your system starts attacking other systems and trying to take them down. And in a lot of causes these kinds of botnets, build the basis of new ransomware campaigns , where ransomware crime groups pay botnet herders to upload the ransomware onto all their victims’ computers and just run it there and encrypt all the data.”
Potentially unwanted programs, or PUPs, are another big issue for home users. These are extra programs that come bundled with free software installers and often hook into your web browser with search bars and icons, and might change your homepage and default search engine.
Wosar notes that they aren’t technically illegal, because there’s often a way to avoid them while installing the software you wanted, Windows has taught us to simply click ‘Next’, ‘Next’, ‘Next’ without really paying attention.
Threats to businesses
It’s a different story for business users, who still face a serious threat from ransomware. “Ransomware campaigns there work a lot different than for home users,” says Wosar. “For home users, ransomware campaigns are either part of big spam campaigns where the malware has just been sent to hundreds and thousands of users, and [the writers] just hope that someone is gullible enough to open the attachment and then run whatever was attached to the email.
“For businesses, ransomware is often targeted. That means people try to attack your company in particular. They will look for weak spots in your defences when it comes to internet-facing services, for example. Usually, that is done through insecure remote control features, like RDP (Remote Desktop Protocol) for example.”
Small businesses without their own IT departments often outsource it to other companies, which install remote control software on their clients’ servers. This means they don’t have to send out a technician every time a client needs help, but often the remote access points are poorly secured. Weak passwords, standard user accounts, accounts with more rights than necessary, and unpatched software are all serious risks.
For businesses, ransomware is often targeted. That means people try to attack your company in particular. They will look for weak spots in your defences
Fabian Wosar, Emsisoft
“These ransomware gangs seek out poorly secured remote access points in services in particular, and once they enter the server they will try to pivot from there onto other systems in the local network,” Wosar says. “And if that isn’t successful they will just start encrypting the entire server.”
Ransoms are also typically a lot higher for businesses because the ransomware writers (often rightly) assume they have more money. Potentially, it’s much more lucrative than targeting home users.
“Businesses also always have to deal with APTs – advanced, persistent threats from often state-sponsored groups that try to steal company secrets in particular and gain all kinds of other advantages and insights,” says Wosar.
“I don’t think we will see a lot of big APTs being revealed in the coming years – mostly because a lot of these big campaigns got revealed over the last few years. APTs will continue to be a threat for businesses, but they will try to fly a lot more under the radar with even more targeted attacks and smaller campaigns in order to make sure that all their tools and specialized malware don’t leak.
The other big threat to businesses is spear phishing – a version of phishing that’s highly targeted at a specific business, and even a specific individual, using harvested data to make the attack more believable.
“A classic example is people mimicking the CEO of a company and sending out emails to the accounting staff asking them to transfer money to pay fictitious invoices,” says Wosar. “But these kinds of attacks also work when it comes to infiltrating companies and getting a company owner to run malware on their system. One common method therefore example is to hide malware inside applications. You want to recruit new staff and have some job offers out there, and people send in their applications with malware hidden inside.
“These types of attacks are more prevalent for businesses these days and those are probably the ones businesses want to watch out for the most.”
How to protect your files
“Backups, backups, backups,” says Wosar. “Antivirus software (and even Windows as an operating system) has come a long way when it comes to detecting and preventing ransomware attacks, so it’s a very useful form of defence, but backups are useful not only for ransomware, but they also help you in all kinds of other situations. For example, what if your hard disk fails?”
When backing up your files, Wosar cites the three, two, one rule. You should have three copies of your data, which should be stored on two different devices, on two types of storage, and one of those should be off-site.
For a home user, that might mean having your photo collection on your PC’s internal hard drive, then making a scheduled backup to an external hard disk, and syncing those backups to a service like Dropbox, OneDrive or Google Drive.
“Keeping your systems up to date is very important, especially as a business, and especially on the systems that can be reached from the internet directly,” Wosar says. “WannaCry, for example, was a very popular ransomware family that used publicly available exploits to exploit systems, and servers in particularly that were accessible from the internet. People didn’t install the patch, so they became infected within literally within minutes of being connected to the internet.”
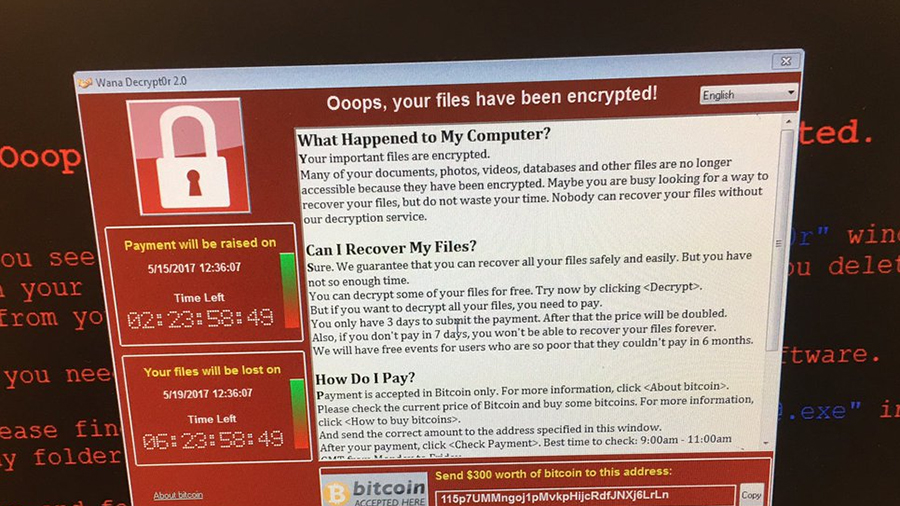
By not installing the necessary security patch, businesses left themselves vulnerable to WannaCry
If you use a company to manage your IT systems remotely, it’s important to reduce the attack surface as much as possible. Make sure there are proper password policies in place, and ensure passwords are long, complex, and not being re-used on different sites.
“At the very least, switch from the default port from the default RDP port to a different one so your system doesn’t automatically light up in a simple port scan, advertising to the outside that this server is using RDP,” says Wosar.
“When it comes to these outsourcing scenarios, often it’s simply not necessary for RDP to be available to the entire internet. Ideally, it should only be accessible to the outsourcing company that you asked to take care of your systems, so take advantage of firewall rules to limit accesses to your servers and to the remote access points in particular, to lock that down as much as humanly possible.
How to decrypt your files
If your files are encrypted, the most important thing is not to remove the ransomware executable file – no matter how unintuitive that sounds. It’s fine to disable it by quarantining it, and disabling the autorun references so it doesn’t start automatically, but don’t get rid of it altogether.
“The first step of trying to figure out whether or not your files can be decrypted without paying the ransom is looking into the ransomware executable to find out exactly what it did to your files,” says Wosar. “And that becomes so, so much more difficult when people remove the infection, because then you have to try to find the one ransomware files out of the millions upon millions of ransomware files out there that encrypted your data, which makes the whole process a lot more difficult.”
If you don’t have a backup of your original files, he recommends making one of the encrypted ones – however strange that sounds.
“We did have quite a few cases where, once the ransomware campaign shut down, the ransomware authors released the keys for free. So if you don’t need access to your files right away, or if you are in the situation where it would be nice to get your files back, but it’s also not that important to you that you would be willing to spend money on getting them back, to just keep the encrypted files around in your backups.”
You might also be able to decrypt your files is law enforcement are able to seize the criminals’ servers, as has happened several times in the past.
The first step of trying to figure out whether or not your files can be decrypted without paying the ransom is looking into the ransomware executable to find out exactly what it did to your files
Fabian Wosar, Emsisoft
If you’ve been hit by ransomware, you might discover that there are several companies around that claim to be able to restore encrypted data, whatever the infection. However, they aren’t always what they seem, and many work as a kind of middle-man, taking your money and handing it to the ransomware writers.
Wosar doesn’t have a problem with these companies if they’re very transparent about what they’re doing – essentially taking out the potentially tricky step of obtaining Bitcoin to pay the ransom and handling the decryption.
“I don’t mind if they are open about that,” he says, “but a lot of people aren’t, and a lot of people pay those companies a shit-ton of money, thinking, ‘Oh, but at least the ransomware author doesn’t get the money’ but in reality they do. You just paid the ransom and some extra for the data recovery company.
“You also have to keep in mind that these ransomware campaign owners actually offer kind of an affiliate program to these data recovery companies. So if you convince your customers to pay the ransomware, [the authors] only take 60% of the thing and you take the other 40% and you can either hand that down to make your service look more legit by asking for less than the ransomware author did, or just take it as a bonus – it’s a profit for you.”
Wosar has even been approached by authors asking if he could ignore their ransomware campaign in exchange for a share of the profits, or suggesting he tell victims there’s no alternative but to pay, and offering him an affiliate link.
Victims are even offered discounts if they leave positive testimonials on support forums like BleepingComputer, assuring other users they they’ll get their files back if they pay.
Emsisoft has released free decryption software for many common types of ransomware (together with details to help you identify the type you’ve been infected by), plus a step-by-step guide for removing it safely.
If there’s no decryptor available for your infection, Emsisoft’s forums offer a free ransomware first-aid service (even if you’re not an Emsisoft customer). Check out this post for the procedure you need to follow.
Powered by WPeMatico